Whitelisting simulated phishing in Office 365
This guide is intended for administrators to allow simulated phishing from Secure Practice.
Last updated: 3 July 2025
You need a security administrator role in Office 365 to be able to complete this guide.
Go to https://security.microsoft.com and login with your administrator account.
In the main menu (left navigation), find «Policies & Rules».
Click the «Threat policies» link in the list that comes up, to reveal the following:
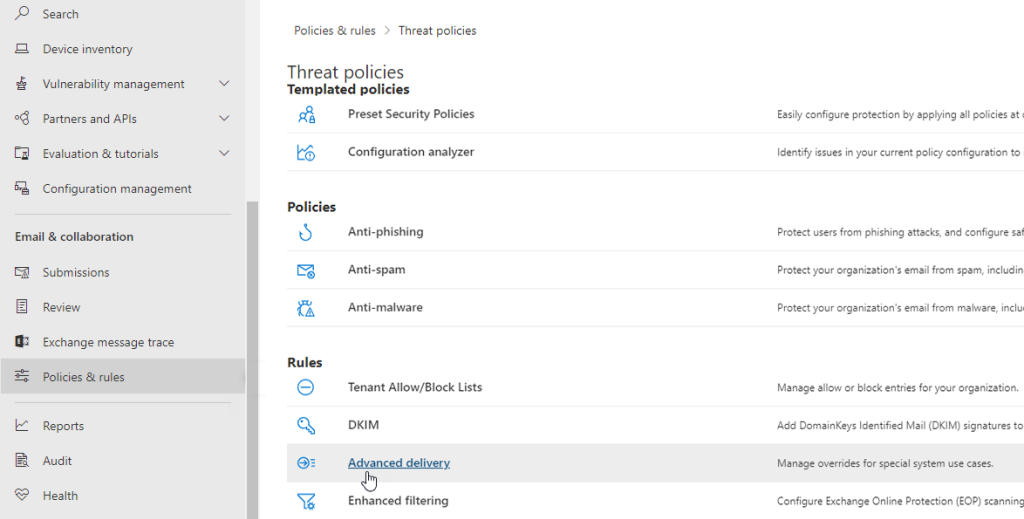
Here, click on «Advanced delivery» to manage overrides for special system use cases.
On the next page, click the «Phishing simulations» tab in the horizontal navigation:
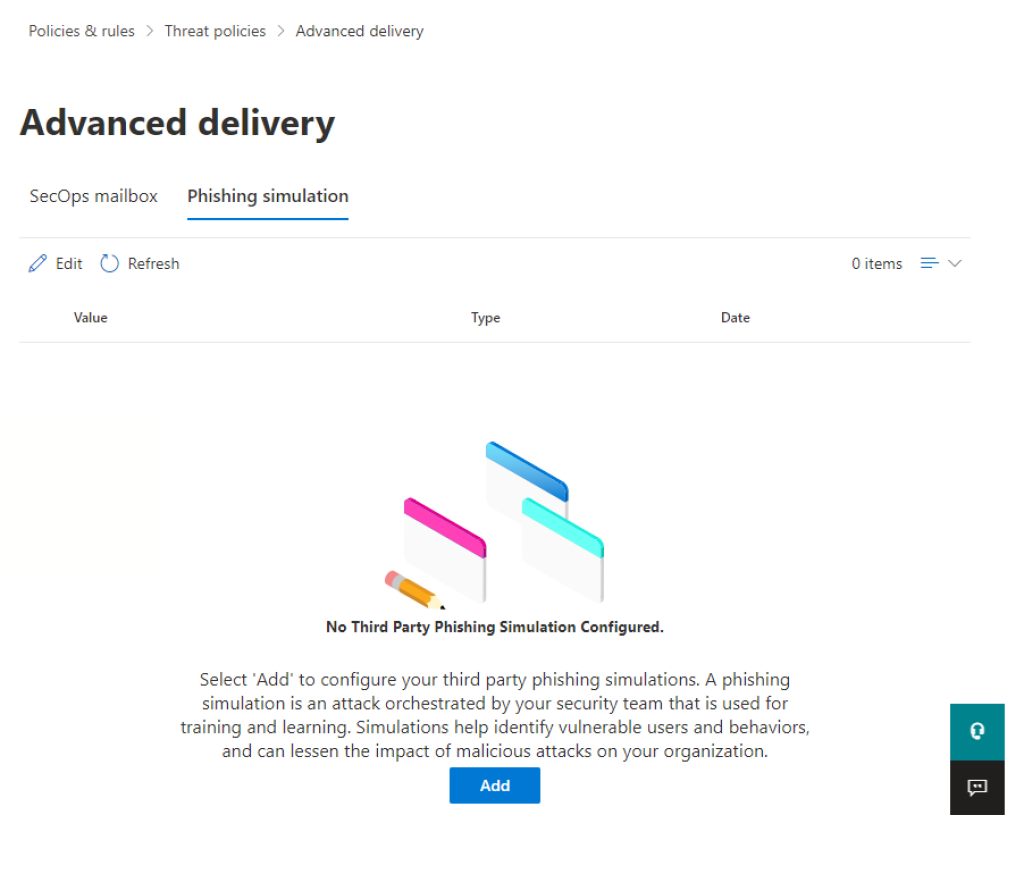
This is where Microsoft allows us to configure the rules we need.
Click the blue «Add» button (see above) to configure this for the first time.
Alternatively, click the the «Edit» button (pencil icon, see below) if a policy already exists.
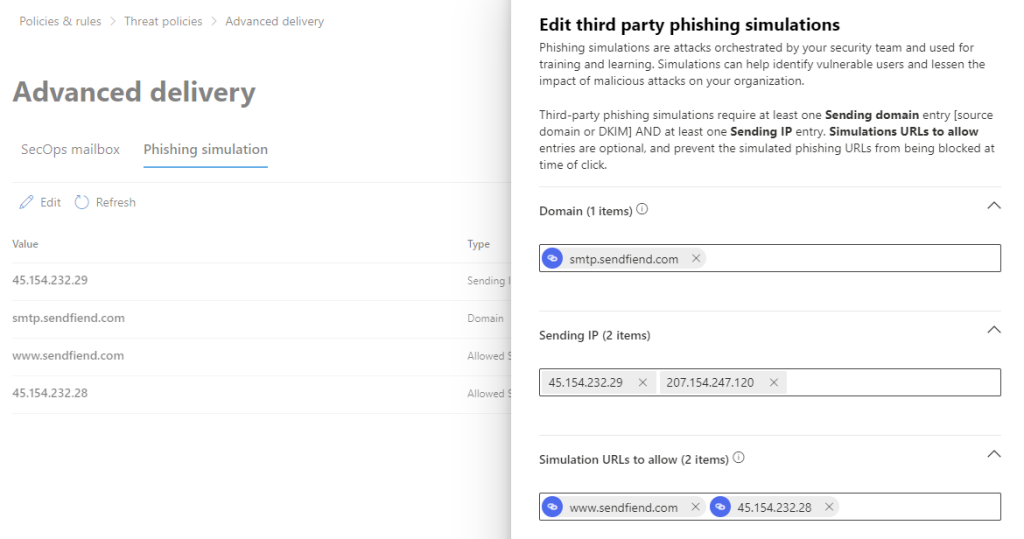
In the «Domain» field, insert the following:
smtp.sendfiend.com
In the «Sending IP» field, insert the following:
45.154.232.29
92.62.34.213
207.154.247.120 (to be discontinued October 2025)
If you have enabled IPv6, these addresses should be added as well:
2a02:2c8:1:400::29
2a02:2c8:1:400::34:213
The last field «Simulation URLs to allow» is optional, but is recommended to include whatever URLs for domain names you are going to use for landing pages in your phishing simulations. Please note you can up to 30 domains here, we recommend that you begin with the IP address (and primary DNS alias) used by our phishing websites:
45.154.232.28
www.sendfiend.com
For IPv6 enabled environments:
2a02:2c8:1:400::28
You may continue to add domains to be used with the phishing simulator, from the list below:
sendfiend.com
4qw.nl
mediapage.eu
nefflix.it
onebrive.com
passordmyndighet.no
sitestoragesharing.nl
telecomservic.es
webhostnet.net
aflassian.com
ctrypo.com
feedbackhubs.com
fiendsend.com
formswebs.com
helloprecious.eu
hotsocl.com
maxtax.ch
metafaceinsta.com
microsott.no
mstf.it
nytinnes.com
passwordauthority.eu
preciousforever.eu
publiclottery.eu
qnaii.com
qxqc.org
salest0rce.com
(Web domains in the first column above were the only ones used up to December 2022.)
Failing to add a domain in this step will not prevent emails from being delivered to recipients. However, with Microsoft Defender for Office 365, links may be blocked by Outlook whenever users click on them, regardless of disabling rewrite rules.
For organizations using Defender for Office 365, you may still also need to whitelist links from rewriting with Safelinks, so that they are not blocked during redirect in people's browsers also.
In addition, you may need to complete the whitelisting in Defender for Office 365 guide.