Bypassing Microsoft Defender for Office 365
This guide is intended for administrators to allow simulated phishing from Secure Practice.
In addition to Exchange, your company may be using other products for filtering incoming email, including Microsoft Defender for Office 365, formerly known as Advanced Threat Protection (ATP).
There are basically two steps to configure achieve effective whitelisting for links, whereas the first deals with links getting rewritten on-the-fly when they are clicked inside Office apps, whereas the second deals with disabling rewrites for email messages themselves.
Defender for Office 365
First of all, open https://security.microsoft.com and click «Policies & rules» in the main navigation.
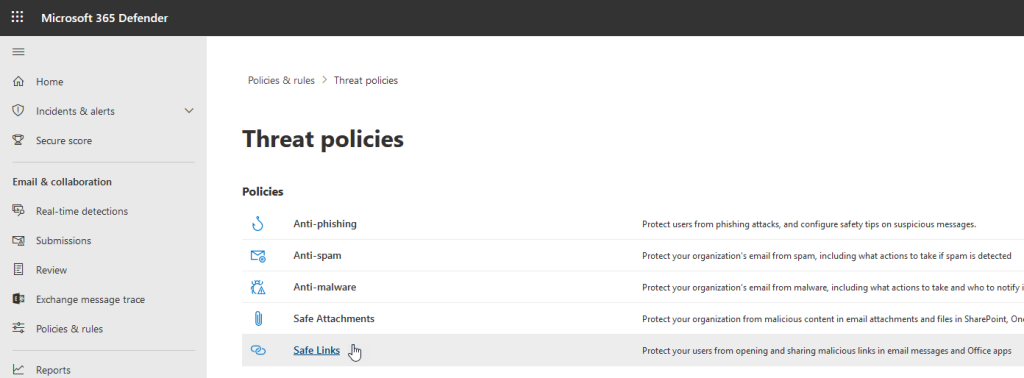
Then, select «Safe links» (below «Policies»), and you will see a list of policies for rewriting links.
If the policy list is empty, create a new policy with «Create» and ensure all relevant users/domains are included in its scope.
If you have a policy here already, click the policy entry to reveal its full details and a link «Edit protection settings» (scroll a bit down), to continue:
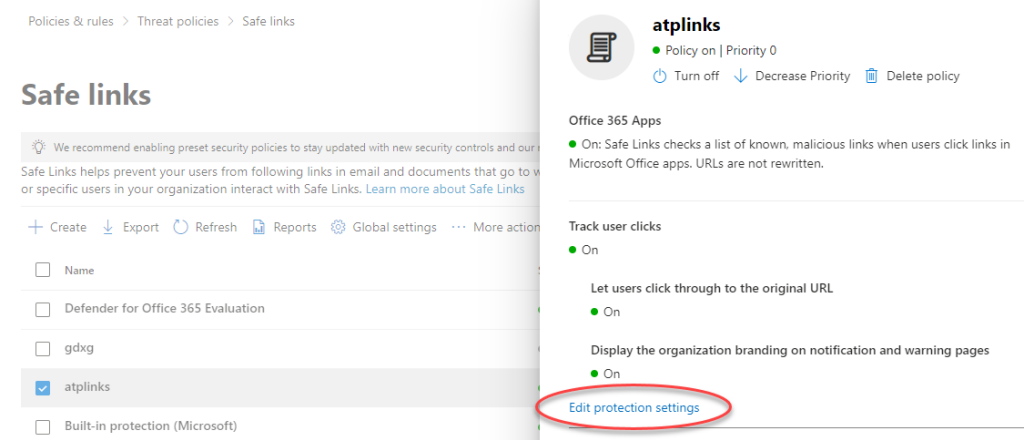
Again, scroll a bit down until you find the section «Do not rewrite the following URLs», with a form to add new URLs:
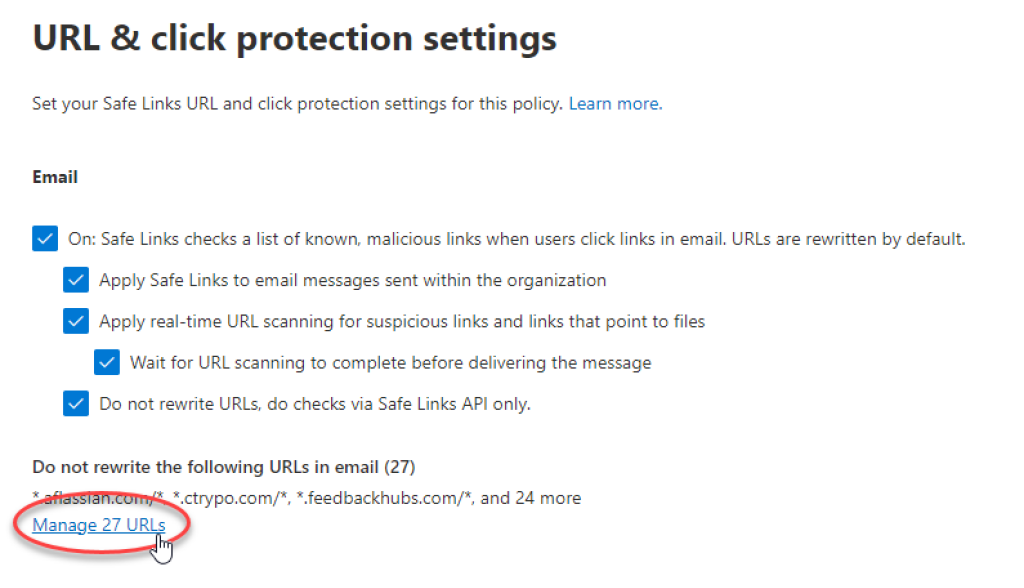
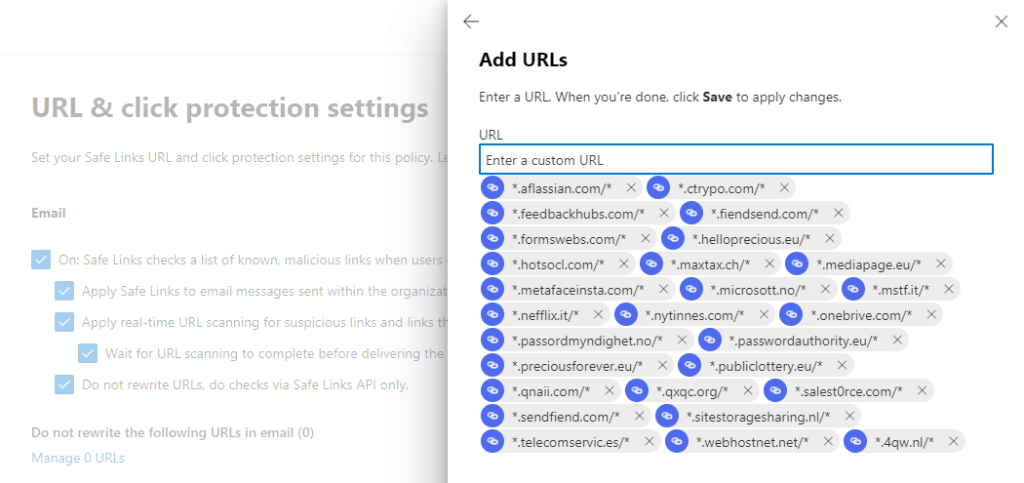
In this list, make sure to add all web domains to be used with the phishing simulator, including:
.sendfiend.com/
.4qw.nl/
.mediapage.eu/
.nefflix.it/
.onebrive.com/
.passordmyndighet.no/
.sitestoragesharing.nl/
.telecomservic.es/
.webhostnet.net/
.aflassian.com/
.ctrypo.com/
.feedbackhubs.com/
.fiendsend.com/
.formswebs.com/
.helloprecious.eu/
.hotsocl.com/
.maxtax.ch/
.metafaceinsta.com/
.microsott.no/
.mstf.it/
.nytinnes.com/
.passwordauthority.eu/
.preciousforever.eu/
.publiclottery.eu/
.qnaii.com/
.qxqc.org/
.salest0rce.com/
For more information on the syntax when entering these whitelisting rules, please refer to Microsoft's official documentation.
Exchange mail flow rules
Before you continue, make sure you have completed the Exchange whitelisting guide, which allows you to copy and just slightly tweak mail flow rules you have already created.
Do you prefer PowerShell? Click to see the scripted version of this guide
First, connect with PowerShell to a new admin session in Exchange. The following will work with Exchange Online (Office 365), see documentation:
1Import-Module ExchangeOnlineManagement Connect-ExchangeOnline -UserPrincipalName <ADMIN EMAIL>Then, after authenticating, create two new transport rules with the commands below:
1New-TransportRule SecurePracticeBypassATPLinks -SenderIpRanges "207.154.247.120","206.189.251.203","159.89.9.35","92.62.34.213" -SetHeaderName "X-MS-Exchange-Organization-SkipSafeLinksProcessing" -SetHeaderValue "1" New-TransportRule SecurePracticeBypassATPAttachments -SenderIpRanges "207.154.247.120","206.189.251.203","159.89.9.35","92.62.34.213" -SetHeaderName "X-MS-Exchange-Organization-SkipSafeAttachmentProcessing" -SetHeaderValue "1"Finally, review your overall rule priorities to ensure that there are not any other custom rules blocking the simulated phishing emails before they reach our whitelist rules.
1Get-TransportRuleIf adjustments are needed, please see the official documentation referenced above, or use the Exchange Admin Center as shown below to re-order rules through a web portal.
And congratulations, we are all done with whitelisting in Exchange!
PS! If at some point you need a script to remove our rules again, the following will work:
1Remove-TransportRule -Identity "SecurePracticeBypassATPLinks" -Confirm:$false Remove-TransportRule -Identity "SecurePracticeBypassATPAttachments" -Confirm:$falseIn Exchange Admin Center, click on «Mail flow» and then «Rules» in the main menu.
Select the «Bypass junk» rule, and click the «Copy» button in the toolbar above it.
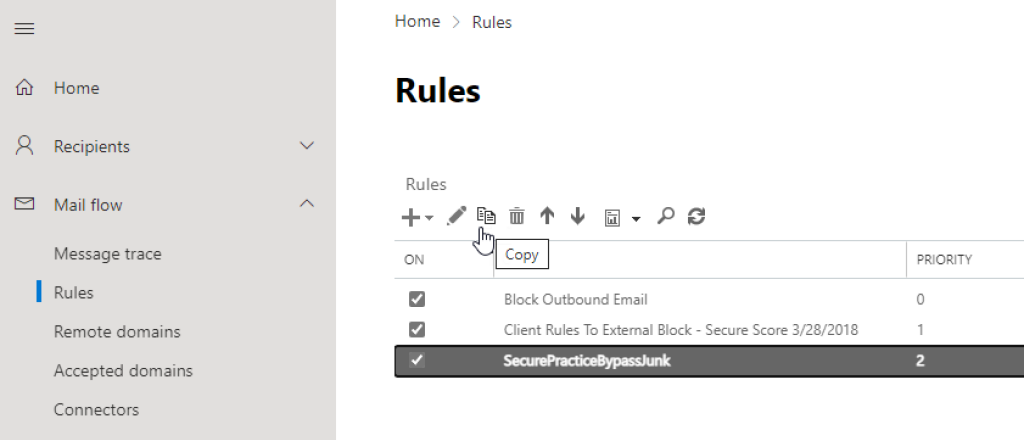
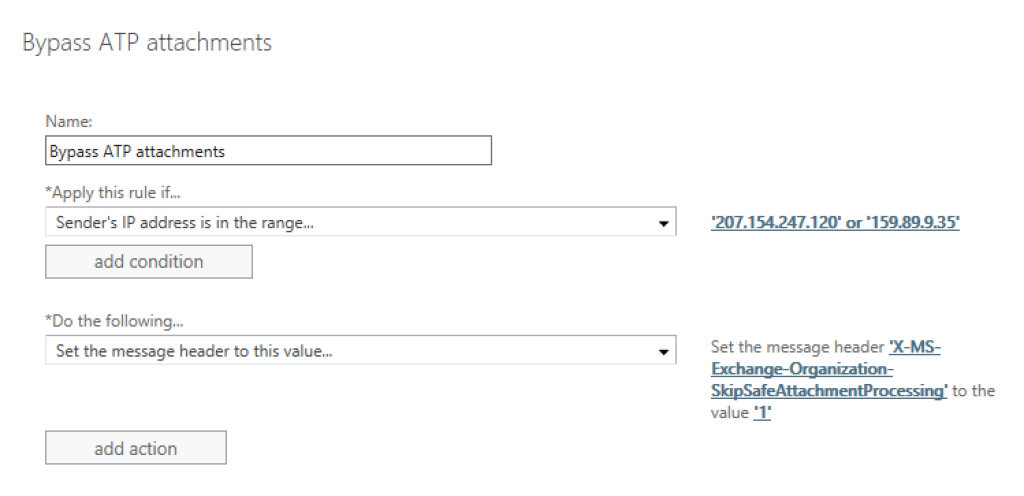
Rename the rule to «Bypass ATP links», and remove the «Set the spam confidence level (SCL) to…» action.
Then, click on the rule property «X-MS-Exchange-Organization-BypassClutter», and replace it with «X-MS-Exchange-Organization-SkipSafeLinksProcessing».
Similarly, change the header value from «true» to «1», and save the updated rule.
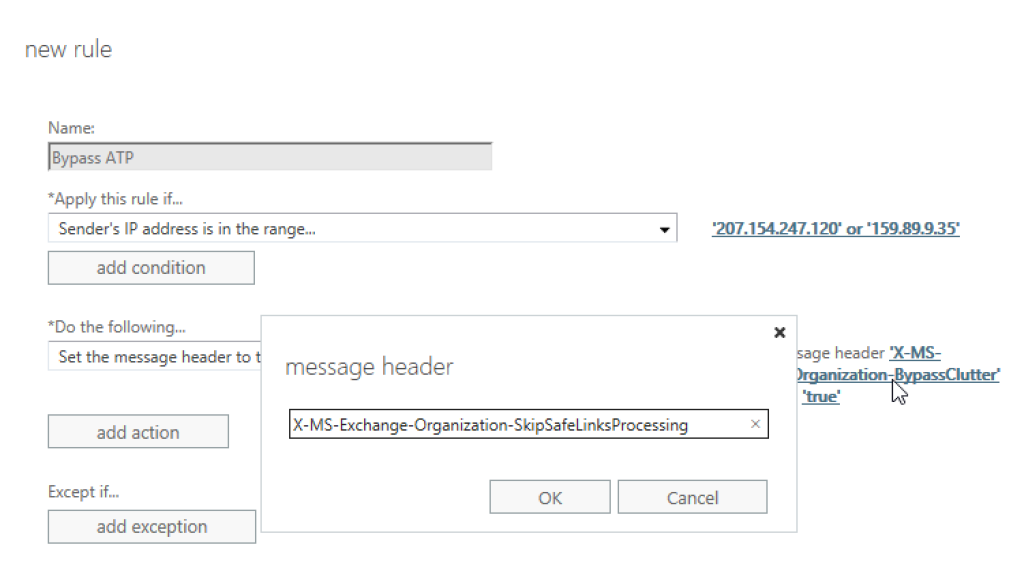
Finally, repeat the copy action with on the rule you just created, and rename the final rule to «Bypass ATP attachments».
Now, set the rule property to »X-MS-Exchange-Organization-SkipSafeAttachmentProcessing», and save the new rule.