Whitelisting simulated phishing in Google
This guide is intended for administrators to allow simulated phishing from Secure Practice.
You need an administrator role in Google Workspace Admin Console to complete this guide.
Go to https://admin.google.com and login with your administrator account.
In the main menu (left navigation), find «Apps», «Google Workspace», and then «Gmail».
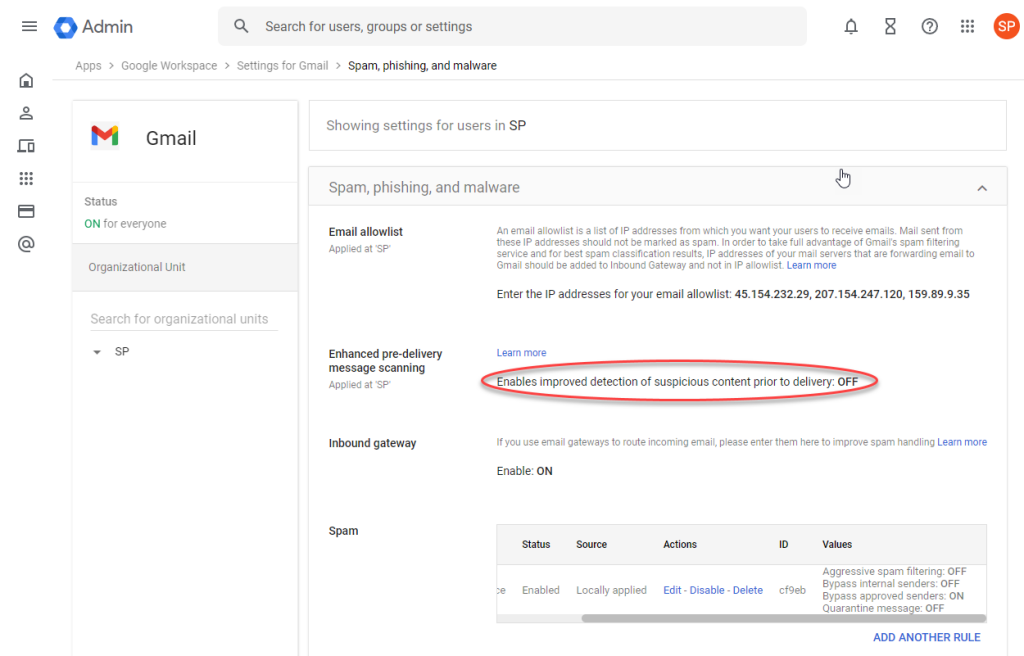
Click the «Spam, Phish and Malware» section in the list which appears:
Here, click on «Email allowlist» to manage IP addresses to always allow email from:
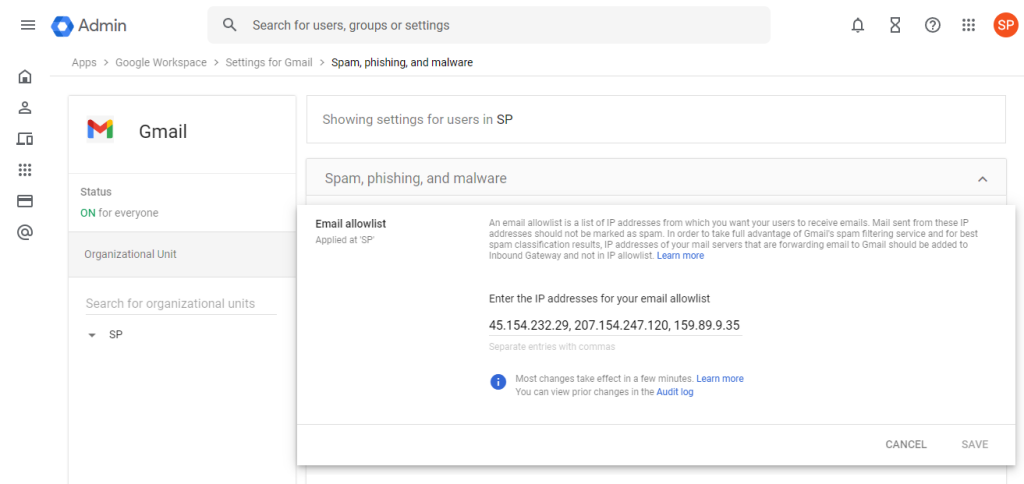
For your email allowlist, enter the following IP addresses, and click «Save»:
45.154.232.29, 92.62.34.213, 2a02:2c8:1:400::29, 2a02:2c8:1:400::34:213, 207.154.247.120, 159.89.9.35
The last two addresses are being discontinued Oktober 2025.
The next step involves a configuration which makes Gmail consider SMTP servers on these very same IP addresses to be «internal», meaning that there will not be performed any verification of SPF or DMARC, and end-users will accordingly never see warnings about the authenticity (or lack of thereof) from the Gmail interface.
Scroll down to the «Inbound gateway» section, to «internal» inbound gateways:
Click the blue «Enable» button (see below, click image to enlarge), if not already enabled.
Add the three IP addresses in the list for «Gateway IPs»:
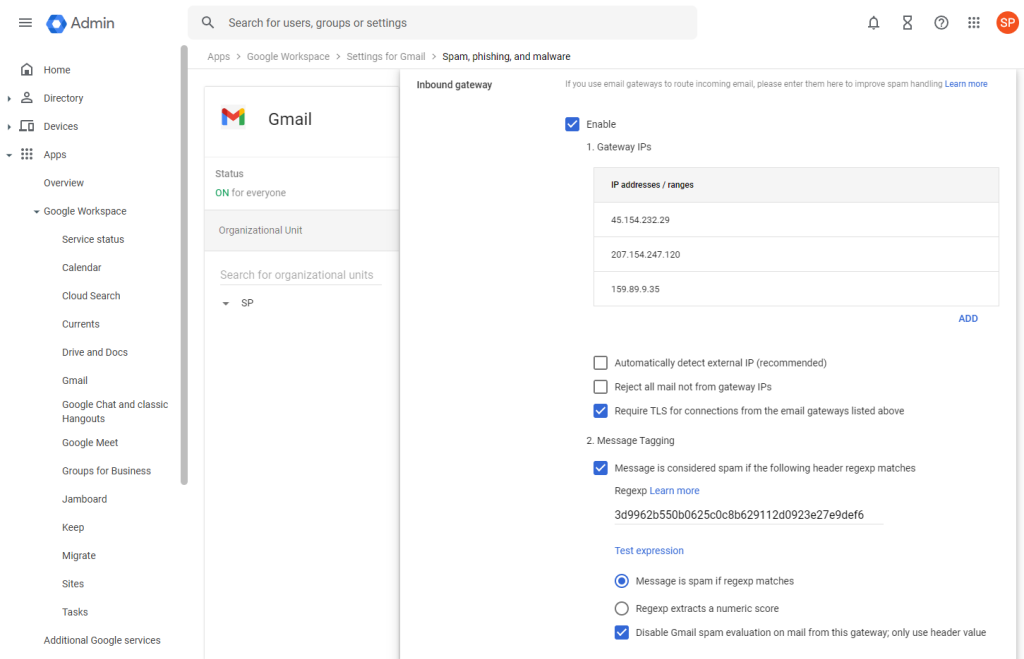
In the settings below, feel free to require «TLS for connections», but do not «reject all email not from email gateways listed» unless you really intend to do this (i.e. never, unless both gateway IPs were specified and this setting was enabled already) – otherwise all email delivery will stop.
Then, in the «Message Tagging» section, do the following:
Tick the box to say «Message is considered spam if the following header regexp matches», which allows us to disable Gmail spam evaluation further down below.
Add a random text value to the «Regexp» field, something unique which is also unlikely to occur in any email (and do not re-use our value from the illustration)
Tick the box «disable Gmail spam evaluation», which will now apply to our IP addresses.
When you have saved the inbound gateway settings, continue to the «Spam» section. Here, we can ensure that emails do not end up in the spam folder, regardless of content.
Click «Configure» to create a list of approved senders:
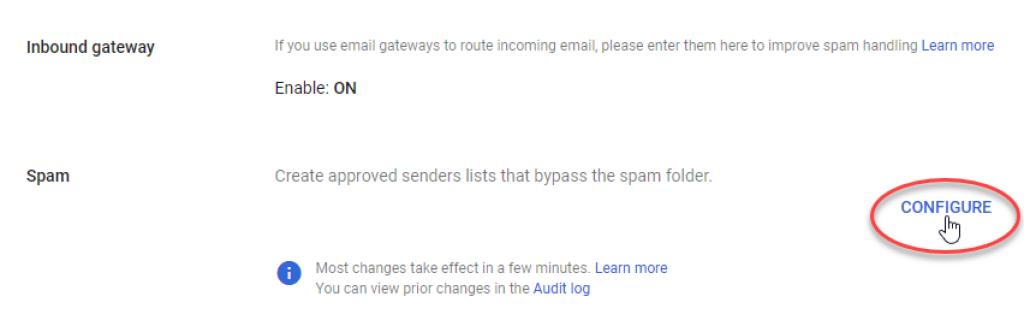
Continue with ticking the box for «Bypass spam filters for messages received from addresses or domains», and then click «Create or edit list» to define a list of approved senders:
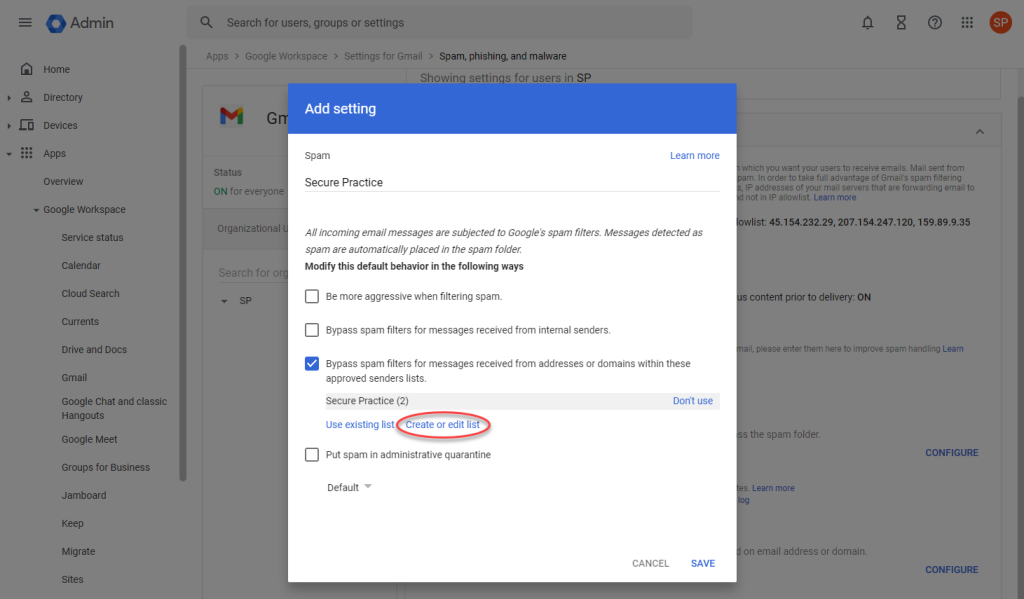
In a new list, add smtp.securepractice.co and smtp.sendfiend.com as address entries
For maximal flexibility, uncheck the toggle for «Authentication required» on the latter one:
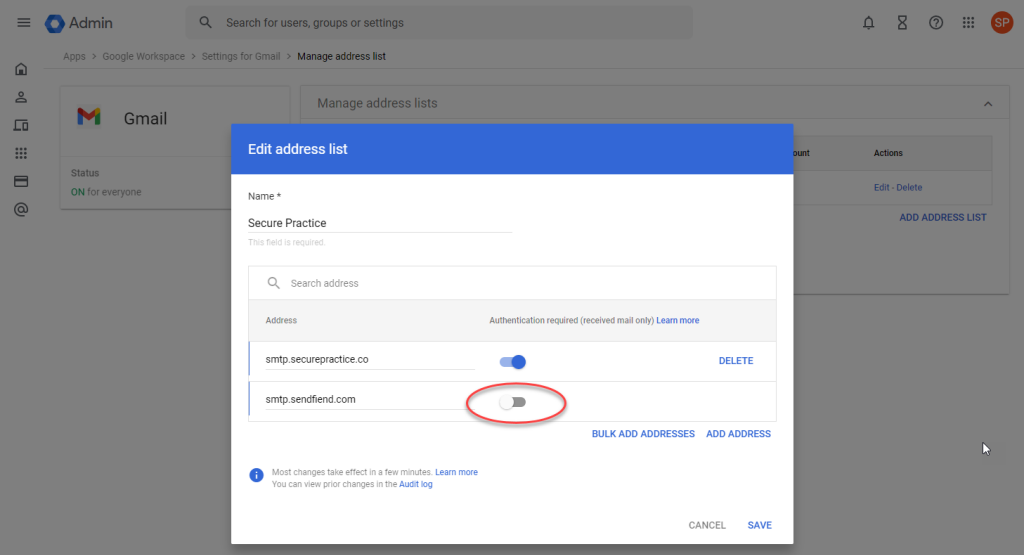
Save the address list, and save the new spam bypass policy setting to complete your setup.
At this point, you should be finished with configuration, and you can proceed with testing.
In their Gmail service, Google offers a feature called «Enhanced pre-delivery message scanning», for improved security. While we do not recommend disabling this feature permanently, doing so temporarily can enable quicker verification of your configuration.