Small security teams face the same threats as everyone else, just with fewer hands on deck.
Over the years, we’ve seen how the best awareness managers turn that reality into results, blending automation, empathy, and focus to keep learning alive.
Today, we look at what small security teams do differently and the practical tactics awareness managers use to make limited capacity go further.
What research tells us about small awareness teams
You don’t need a big team to make a big difference, and the data proves it.
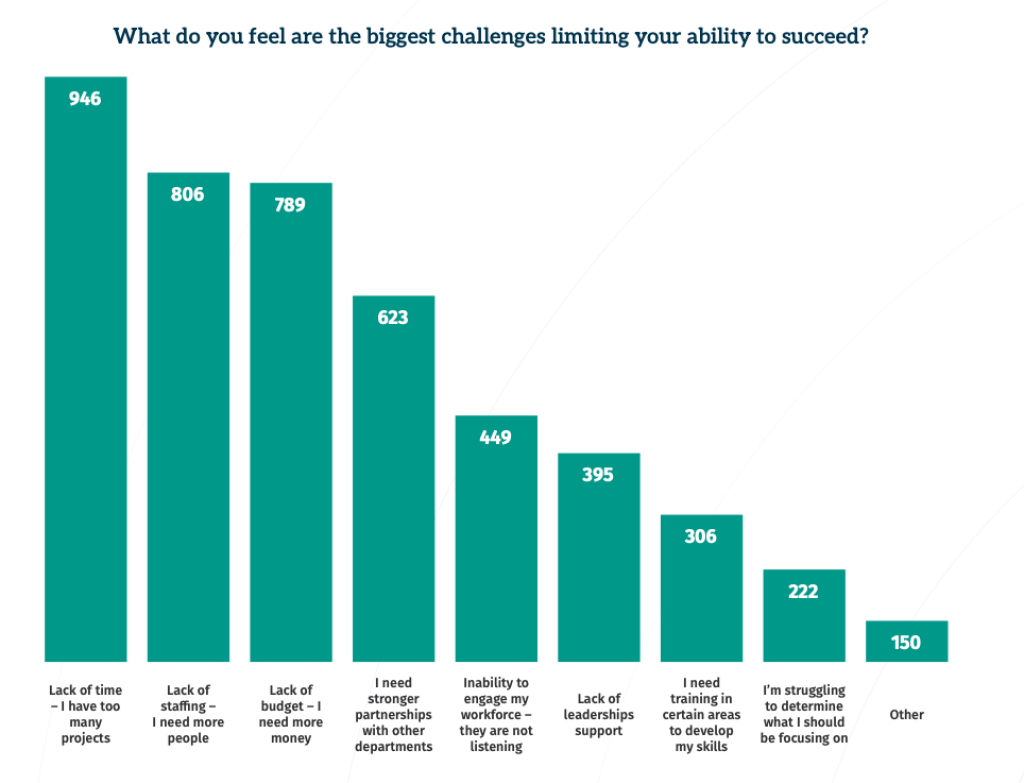
Every year, the SANS Security Awareness Report reads a bit like group therapy: a reminder that none of us are alone in feeling stretched thin.
For the sixth year in a row, lack of time and staff sit at the top of the list of program challenges. The research also shows that meaningful behavior change typically takes three to five years—and full cultural change can take up to ten.
That’s a long road for teams that often have fewer than three people to walk it.
Yet the same research reveals something encouraging: small teams achieve remarkable results by:
Automating energy-draining tasks
Using gamified learning that keeps engagement alive
Building partnerships that extend their reach far beyond their size
They do it by leaning on what big programs often lose: trust, creativity, and proximity to people.
6 ways small security teams make a big impact
Behind every strong awareness program is a team that’s learned to do more with less. These awareness managers are often juggling it all and proving that culture isn’t built by capacity, but by connection.
These are some of the habits that make it possible: the simple, practical moves that scale culture without burning people out.
1. Automate the right things, not everything
For small security teams, time is always the first thing to run out.
Security awareness automation helps you make the most of it by handling routine work in the background freeing you to focus on people.
It works best when it removes repetition, not connection.
If a task repeats and doesn’t need a personal touch, let the system take it over.
Start with the two ends of your process:
The first mile covers setup: enrolling users, scheduling training, keeping campaigns consistent
The last mile is feedback: quick, supportive responses for colleagues and group-level insights for you
When these parts run on their own, you can focus on the middle: writing, communicating, and building trust with colleagues.
💡 Community wisdom: One awareness professional at TOMRA manages 5,000 people across 44 countries. Coming from HR, they focused on making learning easy and relevant:
“The main task that I’m facing is to see what the needs are, how we need to educate people in terms of cybersecurity, and translate it into an easy language for them to understand,” they said. “The solution we had before wasn’t really efficient, so I introduced a new phishing provider and a whole new e-learning setup.”
By automating phishing simulations and reporting, they freed time for better campaigns, clearer messages, and closer collaboration with managers.
Tip: Save your energy for the conversations that impact culture. Automate any task that:
Repeats weekly or monthly
Doesn’t require empathy or judgment
Still consumes manual time (like report analysis, data sorting, or reminders)
2. Gamification that runs itself
Gamified e-learning can motivate people without adding to your workload, if it rewards engagement automatically.
Small teams are finding creative ways to make that happen.
People are experimenting with avatars, point systems, and campaign calendars where recognition and prizes keep momentum going with minimal effort.
This type of learning keeps motivation high even when capacity is low, as long as it’s built to run on its own.
A simple, low-maintenance loop might look like this:
| Step | What happens | How to automate it |
|---|---|---|
| 1. Monthly micro-challenge | A short (60–90 second) quiz or scenario is assigned to everyone. | Schedule recurring campaigns in your learning portal. |
| 2. Auto-tracked progress | Points and completion data update automatically. | Use built-in progress tracking in Secure Practice to measure engagement by group. |
| 3. Team-level leaderboard | Progress displays by department or region, not by name. | Enable privacy-friendly dashboards for collective insights. |
| 4. Quarterly recognition | The system announces winners or sends small rewards. | Let automated notifications or reward draws handle recognition. |
Tip: Use our gamified e-learning portal to make learning feel rewarding, with minimal setup.
In Secure Practice, people can track their own progress through chapters and levels, earning points and badges as they go. This visual sense of completion helps maintain motivation—especially for distributed teams that rarely meet face-to-face.

3. Simulations that double as communication
Phishing simulations aren’t just tests. They’re one of the best ways to start conversations about real threats.
When used well, a simulation becomes a learning opportunity that happens in the moment, not months later in a report.
Several awareness professionals have shared that they now treat every simulation as a message: a chance to tell a story about what’s changing, not just who clicked.
They do it by:
Including quick, friendly feedback right after the click
Sharing real examples of scams or internal incidents (with details anonymized)
Ending with a short takeaway or next step
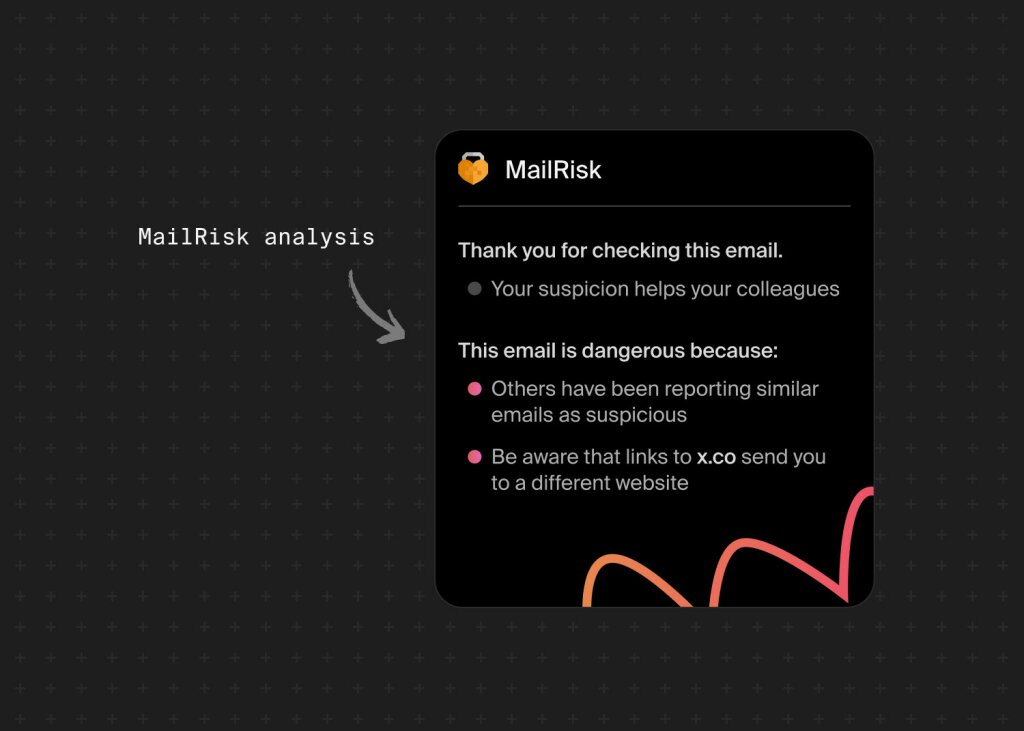
That’s exactly what MailRisk was designed to do.
Instead of waiting for a quarterly report, your colleagues receive instant, supportive feedback when they report or interact with a simulated email. The button sits right inside their inbox—on desktop, webmail, or mobile—so learning happens where mistakes do.
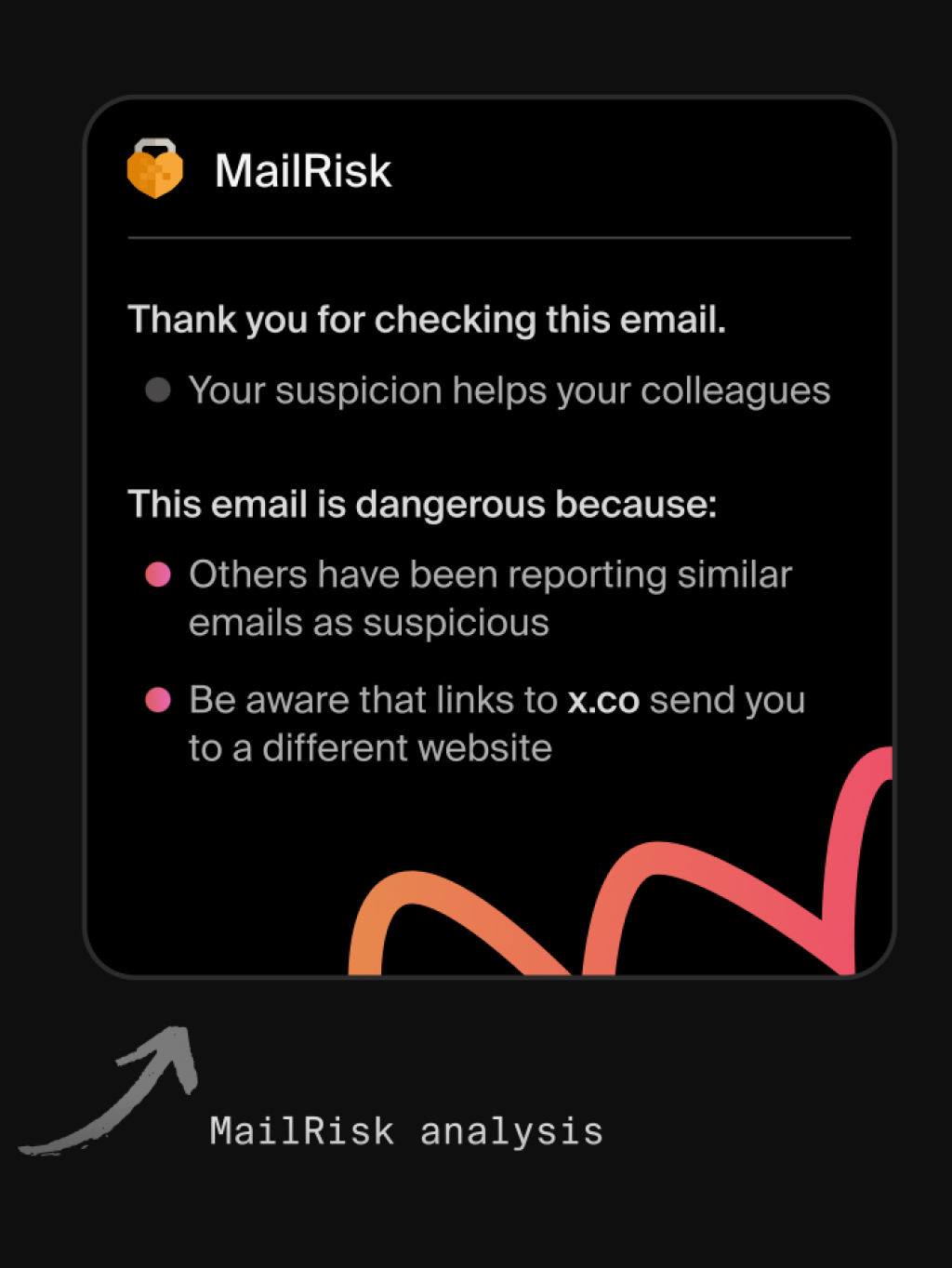
Behind the scenes, MailRisk automatically compares reported messages with those flagged by colleagues and other trusted data sources. When it finds a match, users see right away that their action helped protect the organization and themselves.
For small teams, this approach means one activity serves two goals: learning and engagement.
The simulation teaches while it communicates—no extra campaign needed.
Tip: if building templates and reporting takes you more than 5–10 hours/month, a managed approach is usually cheaper than “free.”
Start simple to learn what works for your people, then upgrade when manual effort starts stealing your time.
Here’s a simple path small security teams can follow as they mature:
| Stage | Focus | Admin effort |
|---|---|---|
| Start | Use the built-in phishing tools in your email or collaboration suite. Reuse templates and send a short “lesson learned” message after each run. | Low |
| Grow | Try a lightweight, self-hosted simulator with ready-made templates and basic reporting. It gives more control without locking you into a contract. | Medium |
| Optimize | When upkeep outweighs results, move to a managed solution like MailRisk. It automates the loop, sending instant, supportive feedback on reports and simulation and rolling results into privacy-friendly group dashboards. | Low (after setup) |
4. Measure what matters and focus where it counts
Security professionals often joke that the hardest part of awareness work is “telling the story behind the spreadsheet.”
One awareness professional shared how their small team started tracking touchpoints instead of output—how many employees read a tip, attended a webinar, or reacted to a post—and paired that with behavioral signals like reporting speed or repeated clicks.
Another summed it up simply: “Touchpoints > assets.”
You don’t need to measure everything, just what leads to real behavior change.
Borrow this simple framework from other professionals, then apply the 80/20 rule: focus on the groups that show the most risk or engagement, not individuals.
| What to track | Why it matters | Example metric |
|---|---|---|
| Touchpoints (emails read, posts viewed, webinar attendance) | Shows reach and relevance | 72% of staff opened the monthly tip |
| Behavior signals (time-to-report, group click rate, completion speed) | Measures change | Reporting speed improved by 30% |
| Consistency (monthly cadence of micro-campaigns) | Builds trust and predictability | 12 micro-campaigns completed this year |
Tip: Focus on two or three behaviors that make the biggest difference to your organization’s risk, like reporting suspicious emails, using MFA, or handling data safely.
Automate or drop everything else. Partner with HR or internal comms to reuse their existing channels instead of building new ones, and let AI handle small tasks like summarizing reports or drafting reminders—but always keep a human eye on what it creates.
5. Dashboards that focus on groups, not individuals
Many awareness professionals say they’ve moved away from tracking individuals. Instead, they group data by department, region, or role to spot trends without creating anxiety or blame.
This small shift makes data more useful and far more human.
Group-level dashboards reveal where awareness is growing, where support is needed, and how culture is changing, all while protecting privacy and trust.
This principle is core to how we built Secure Practice dashboards. From day one, our goal has been to help organizations measure human cyber risk responsibly: enough insight to act, but never at the expense of trust.

Individual results are never shown. Instead, we use human risk metrics to help you understand, measure, and manage the cybersecurity risks associated with human actions.
Human risk metrics collect anonymized insights from every interaction with the Secure Practice toolkit, including:
Quizzes, surveys, newsletters and more.
Together, they highlight where learning works and where help is needed, so awareness managers can act confidently without exposing anyone.
Tip: Use group trends like reporting rates or simulation performance to guide your next steps.
Share results with managers (“Your department improved reporting by 25%. Great progress!”), and replace one-on-one correction with team-level coaching.
That’s how dashboards become tools for encouragement, not inspection.
6. Know when and what to outsource
Even the most efficient teams hit a limit.
There are only so many hours in a week, and most awareness professionals are already juggling training, reporting, and communications on top of daily requests.
That’s why many small teams choose to outsource parts of their program—not to hand it over, but to buy back time for the work that truly needs a human touch.
💡 Community wisdom: In the security awareness field, burnout doesn’t come from caring too little, but from caring without enough capacity.
In the 2025 SANS survey, over 35% of professionals said they love the human side of cybersecurity but want to change companies. That says a lot: people aren’t leaving the mission—they’re leaving environments that don’t give them the capacity to do it well.
Outsourcing can help when it’s done with intention. You stay in charge of the message, the “why,” and how it fits your culture, while partners or tools handle the repetitive or technical parts that drain your team’s time and energy.
Here’s how smart awareness managers delegate without losing control:
Automate or outsource repetitive work like report analysis, template updates, or campaign scheduling.
Keep communication and feedback in-house; those are the parts that make awareness programs truly effective.
Choose partners who respect your privacy principles, especially if data is involved.
Many awareness teams use external expertise for creative campaigns, interactive cybersecurity exercises, or data analysis but still lead the strategy and communication internally. That balance keeps programs consistent and authentic—two things that can’t be outsourced.
Tip: Buy back time in bursts.
Commission a creative partner once a quarter for a themed kit: visuals, templates, and ready-to-use messages you can reuse all year.
Use a ready-made e-learning library for core topics like phishing and passwords, while you focus on culture-specific communication.
Let Secure Practice handle phishing simulations and feedback, so colleagues get instant, supportive learning moments while you stay focused on connection.
Working smarter means protecting both people and time
If time and headcount were the keys to effective security programs, most of them would have succeeded by now.
The truth is, progress comes from focus: a few security tools that run on their own, a system that protects privacy, and a rhythm that turns effort into progress.
Small security teams are proving that clarity, trust, and creativity go further than capacity ever will.
That’s the kind of focus we help teams build at Secure Practice: practical tools, privacy-first insight, and the confidence to turn limited time into lasting impact.
Small teams don’t have to think small
Secure Practice helps small teams make security personal, scalable, and sustainable, so you can focus on people, not spreadsheets.
FAQs about small security teams
What does a security team do?
A security team protects an organization from cyber threats and physical risks.
Their main functions include risk assessment, vulnerability management, and incident response, all aimed at reducing downtime and preventing cyberattacks.
What are the different types of security teams?
Security teams vary by size and structure but usually cover a few core functions:
Security operations (SOC): Monitor systems and respond to incidents in real time.
Risk and compliance: Ensure the company meets standards like ISO and GDPR.
Awareness and training: Build incident preparedness and resilience against phishing and social engineering.
Physical security: Safeguard people and premises.
Secure Practice complements these by focusing on the human side of security, turning complex risks into actionable insights that reduce vulnerabilities.
How much is a small security team?
A small security team often includes two to five people, covering multiple security functions such as risk management, vulnerability monitoring, and awareness campaigns.
For small business cyber security, one person or a small team often handles everything from firewalls to awareness training. It's usually more cost-effective to combine internal expertise with specialized tools or service providers.
Platforms like Secure Practice support these teams by automating phishing defense, gamified e-learning, and privacy-friendly human risk metrics—all without the need for extra staffing.
How can a small security team effectively manage cybersecurity threats?
Small teams succeed by focusing on what matters most: prevention, visibility, and communication. That means:
Running regular vulnerability management and risk assessments
Using tools that provide real-time insights into phishing and human risk
Collaborating with trusted service providers for specialized support
Hands-on training helps small teams manage cyber security threats through tools like phishing simulations, feedback loops, and anonymized dashboards, letting them act fast without sacrificing trust or privacy.
Is it difficult for small teams to set up security software?
Not today. Modern security services are built with small teams in mind, offering cloud-based setups, simple integrations, and intuitive user experiences. Security awareness solutions can be deployed quickly, connecting easily to existing email and collaboration tools.
They help automate reporting, deliver training, and surface insights about risky behaviors—all with minimal staffing or technical overhead.
How does security software help defend against phishing attacks?
Phishing remains one of the most common entry points for cybercriminals. Effective security software identifies and filters suspicious emails before they reach users, and turns mistakes into learning moments when they do.
Tools like MailRisk automatically analyze reports and provide instant, supportive feedback that reinforces awareness across the company.
Do small and medium enterprises (SMEs) need a Security Operations Centre (SOC)?
Not necessarily, but they do need the functions a SOC provides: threat intelligence, incident response, and vulnerability management.
For many small businesses, outsourcing these services or using integrated tools is more cost-effective than running an in-house SOC.
Platforms like Secure Practice fill the gap by offering insight into human-related risks and behaviors—the side of security operations that traditional monitoring tools can’t see.
By pairing these insights with managed detection and response providers, SMEs can maintain strong security management without building a full-scale SOC.