There’s never enough time to plan. Budget is tight. And many awareness efforts feel disconnected from people’s daily work.
We’ve pulled together three practical cybersecurity exercises for employees you can start using today—even with a small team. These ideas are low-prep, low-cost cybersecurity training options that help you build security awareness without adding stress.
And with the right tools, like Secure Practice’s training platform, you can build real engagement without burning out your resources.
Why smaller organizations struggle with cybersecurity exercises
Cybersecurity exercises are the bridge between knowing about threats and actually being able to handle them—whether they show up in your inbox, hit your network, or disrupt your workday.
And yet, for many small and medium-sized organizations, turning good intentions into action feels out of reach.
They know they need cyber awareness training, but they assume it requires complex scenarios, expensive software, or a full-time security team. Others believe cybersecurity exercises are only useful for large enterprises.
In reality, simple cybersecurity activities—done consistently—can dramatically reduce human risk and improve everyday decision-making.
Regular training pays off. In fact, 80% of organizations say security awareness programs reduce employees’ susceptibility to phishing attacks, while some simulated phishing studies suggest that with consistent training, phishing click rates can drop.
But the benefits go beyond just threat prevention. Teams that practice cyber incident response tend to:
Make faster, more confident decisions during emergencies
Build automatic security habits over time
Improve cross-functional coordination between departments
With platforms like Secure Practice, even organizations without dedicated security staff can implement meaningful, human-centered cybersecurity exercises that fit into real workflows and grow with your team’s needs.
The 5 types of cyber security training that actually work
Cybersecurity training is a system for building real-world capability. But not all training works the same way. The most successful programs combine different types of learning to meet people where they are, across roles and risk levels.
Here are five core types of cyber security training that have proven effective across organizations of all sizes:
Awareness-building: quick phishing simulations, myth-busting quizzes, and email tips that keep threats top of mind.
Skill-building: interactive scenarios and cyber tabletop exercises that let people practice safe decisions in realistic situations.
Response coordination: exercises that help departments work together during incidents and uncover communication gaps.
Leadership preparedness: exercises that train managers to handle pressure, brief stakeholders, and make fast, informed decisions.
Culture-building: recognition programs and informal learning that turn secure behavior into everyday habits.
A comprehensive program doesn’t try to do everything at once. Instead, it builds rhythm, with monthly security awareness challenges, quarterly skills-based simulations, annual team-wide coordination exercises, and ongoing culture-building touchpoints.
3 low-prep cybersecurity exercises anyone can run
If you’re wondering how to improve cybersecurity awareness across your organization, the answer isn’t more rules—it’s smarter, more human-centered learning formats.
These three low-prep cybersecurity exercises are designed to fit into real work life. They cover the essential categories found in most effective training programs, including awareness training, incident response exercises, and cyber tabletop exercises.
1. Run a smart phishing test in under 3 hours—no security team needed
Phishing simulations delivered via email are one of the fastest ways to improve threat recognition. They’re one of the most popular types of cyber security training, and you don’t need a big budget or in-house security team to get started.
The key is to make them relevant. Instead of random, generic emails, start with the kinds of scams your team is most likely to encounter.
Work to build threat recognition skills (not just phishing shame)
Before we dive into the specifics of the simulation, we need to talk about why most phishing training fails—and how to do it differently.
Recent research presented at Black Hat 2024 confirms what security professionals have suspected: traditional phishing training often wastes time and may even harm security culture.
The study found that generic, punitive simulations can increase risky behavior rather than reduce it. But here's what the research also shows: the problem isn't with phishing simulation itself—it's with how most organizations implement it.
Erlend Andreas Gjære, our CEO at Secure Practice, co-founded the company after years of studying how real people interact with cybersecurity—first as a research scientist, then as an advisor to businesses and public sector teams.
His research and real-world experience pointed to a gap: most phishing programs focus on who clicks, when what really matters is what people do next.
As Erlend explains in his essay, The Missing Link in Email Security:
Reporting phishing is a security behaviour that involves identifying a threat, stopping yourself from clicking the link, and informing someone else. That’s not just a single step—it’s a small chain of decisions that requires both awareness and confidence.
It’s not enough to test whether people click. You need to help them build up that “small chain” of decisions through relevant examples, timely feedback, and follow-up support.
| Traditional approach (what doesn't work) | Human-centered approach (what does work) |
|---|---|
| Generic templates with no relevance to actual threats | Industry-specific threats based on real attack patterns |
| Punishment-focused "gotcha" moments | Supportive feedback that builds confidence |
| No follow-up support or reporting mechanisms | Clear reporting channels for suspicious emails |
| Measuring only click rates, not behavior change | Focus on building security habits, not testing people |
The missing link in most phishing programs isn't the simulation—it's what happens next. We believe that when someone clicks a simulated phishing link, that’s a learning opportunity.
Here’s how to bridge that gap:
Immediate, supportive feedback: instead of shame, provide context about why the email was realistic and what specific elements to watch for
Easy reporting mechanism: give people a simple way to report suspicious emails, whether real or simulated
Follow-up support: check in with people who struggled, offer additional resources, and celebrate those who reported threats
Behavioral tracking: monitor reporting behavior and threat recognition over time, not just click rates
What makes a good starter simulation?
Start with threat intelligence. Research actual phishing campaigns targeting your industry:
If you're in healthcare, focus on fake medical supply invoices or HIPAA violation notifications
If you're in finance, emphasize wire transfer fraud attempts or regulatory compliance alerts
If you're in education, consider fake IT support requests or student information verification scams
Then, customize for different roles within your organization.
| Role | Realistic email example |
|---|---|
| Executives | “Board meeting agenda” with a malicious calendar attachment |
| HR | Fake resumes with malware or urgent employment verification requests |
| Finance | Wire transfer fraud attempts, fake invoice attachments |
| IT | “Security patch available” emails from spoofed vendors |
| Sales | Fake prospect inquiries with suspicious proposal files |
If you don’t have time to research attacks, Secure Practice makes this easy: our simulated phishing platform comes with pre-built scenarios based on real threats in healthcare, finance, education, and more.
Unlike traditional phishing simulators that focus on catching people making mistakes, Secure Practice emphasizes building positive security behaviors:
Real-time threat intelligence: our simulations mirror actual attacks targeting your industry, pulling design and content straight from actual fraud attempts
Supportive learning paths: when someone clicks, they receive helpful context and next steps, not punishment
Integrated reporting tools: every simulation teaches people how and when to report suspicious activity using MailRisk
Behavioral analytics: we track improvement in threat recognition and reporting behavior, providing a complete picture of security maturity
Our goal is to help train teams that don't just avoid clicking malicious links, but actively contribute to organizational security by reporting threats and helping colleagues stay safe.

What can you do in under 3 hours?
Whether you’re a small business or a growing team, this is a simple cybersecurity activity that delivers a high return with minimal prep.
If you’re just starting out, skip the advanced branching attack chains. One well-targeted email and a short feedback loop can spark the behavior change you're aiming for.
Send an initial simulation to 25% of staff as a pilot group to practice threat recognition and test the realism and difficulty level. Monitor learning progress, and follow up with supportive guidance. Focus on building capability, not catching mistakes.
Then, analyze results and refine your approach based on feedback and performance data.
Finally, launch the full simulation across the organization with clear educational follow-up.
Here’s what that works up to:
| Task | Time estimate |
|---|---|
| Choose 3 templates from Secure Practice or adapt real phishing examples | 1 hour |
| Run a pilot with 25% of staff | 30 min |
| Review reports and send friendly feedback to those who clicked | 1 hour |
| Prep educational follow-up | 15-30 min |
2. Send a 10-minute challenge that teaches habits people actually use
You don’t need an LMS, a security trainer, or a content writer to make people more security-aware. Some of the best learning happens in 10-minute chunks—the kind people can do over coffee.
The “trick” is keeping it specific and practical. Instead of explaining cybersecurity, give people something they can try, react to, or solve.
Take a look at these nine example micro-challenges, organized by topic:
Password hygiene
| Challenge | What it teaches |
|---|---|
| “Create a strong password for a fake banking app in under 2 minutes.” | Real-time password creation skills |
| “Which of these passwords would take longer to crack?” (with brief explanations) | How password strength works |
| “Update one old password this week using your password manager” | Habit-building with secure tools |
Link checking
| Challenge | What it teaches |
|---|---|
| “What 3 things should you verify before clicking this link?” (interactive example) | Pre-click awareness |
| “Which of these URLs is legitimate?” (real vs. spoofed domains) | Visual phishing detection |
| “You got a link from a colleague—how would you verify it before clicking?” | Safe decision-making in realistic communication |
File sharing
| Challenge | What it teaches |
|---|---|
| “Your colleague needs to access a sensitive document. What’s the safest way to share it?” | Secure file-sharing choices |
| “When should you use attachments vs. a secure sharing tool?” | Context-based decision making |
| “Practice sharing a test doc using your org’s approved secure sharing method.” | Reinforcement of compliant behavior |
You can make these micro-challenges work, even without a training department. Just post one per week in Slack, Teams, or your internal comms channel. The format should be:
Visual: use polls, GIFs, quick screenshots, or links to short interactive modules
Simple: make each challenge doable in under 10 minutes
Varied: alternate between questions, decision-making tasks, and quick quizzes
The goal isn’t to test people. It’s to help them build better security habits, which happens through repetition, not pressure.
Make it even easier with Secure Practice e-learning
Secure Practice makes all of this plug-and-play. Our gamified e-learning modules are:
Bite-sized and focused, so people can complete them without interrupting their work
Visual and interactive, turning lessons into memorable mini-games
Language-inclusive, with 14 built-in language options and automatic content translation
Customizable, so you can create your own modules around specific tools, policies, or risks
You can even assign topics based on interests or roles—like giving IT teams a different challenge from marketing or finance.
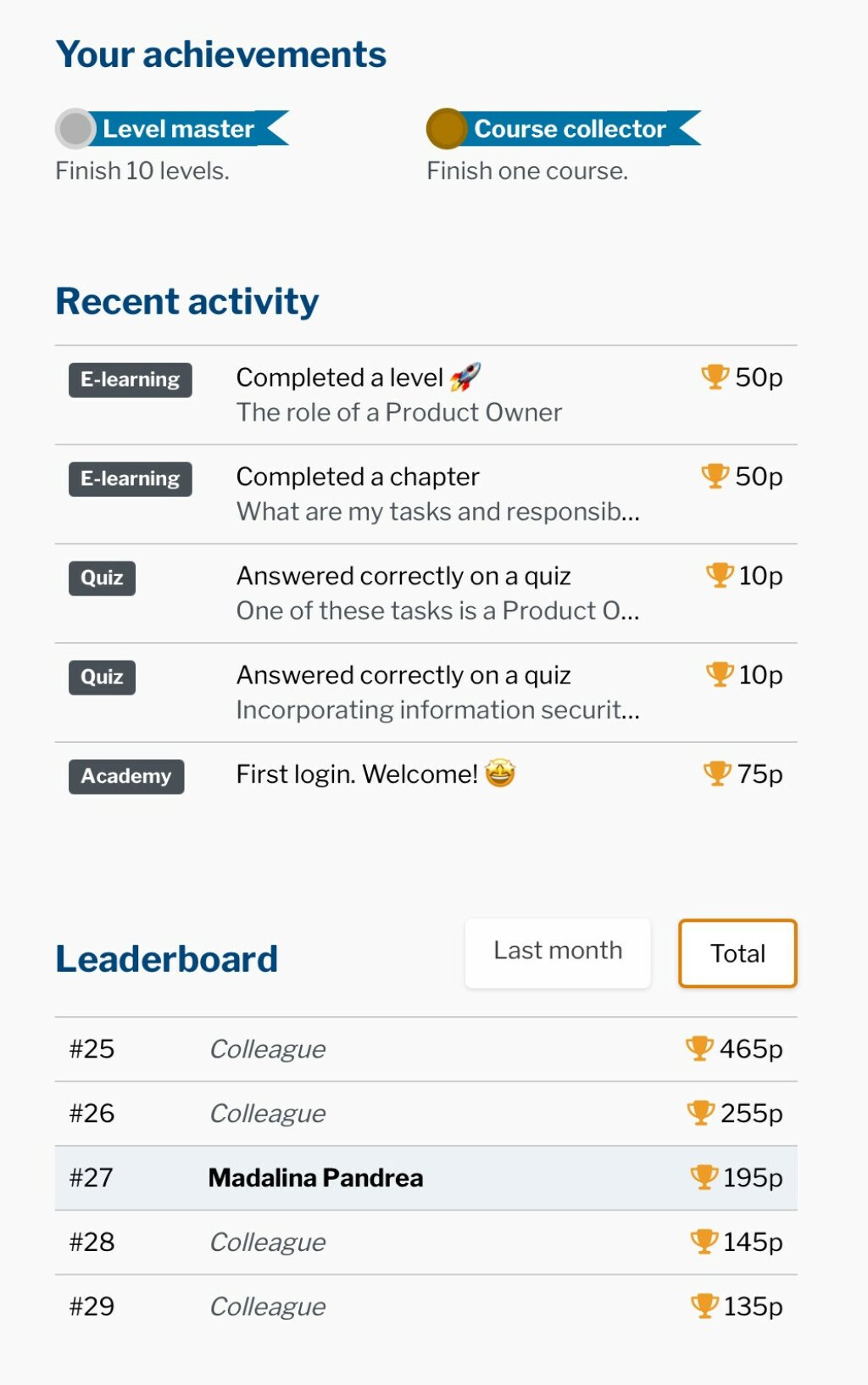
Behind the scenes, Secure Practice uses anonymized behavioral data (like how people engage with phishing simulations or report suspicious activity) to tailor the gamified security training challenges they receive.
Struggling with suspicious links? You’ll get a module on URL verification.
Repeatedly ignoring password hygiene? That person gets a challenge about password managers.
This dynamic targeting ensures people get the right kind of support, while protecting their privacy and avoiding shame or punishment.
3. Walk through a realistic cyber incident, with no tech setup
Traditional tabletop exercises—where teams gather around a conference table to discuss hypothetical scenarios—have been the gold standard for incident response training in large enterprises. But they often require facilitators, formal documentation, and significant time investment.
We're entering a new era of cyber exercises that keep the collaborative discussion benefits while making them accessible to any team size. You don’t need an external facilitator or incident response team. You just need 3–5 people, a 15-minute scenario, and a willingness to talk through “what if.”
One of the most effective scenarios is a ransomware attack. It’s high-stakes but easy to imagine, and every department has a role to play.
This lightweight approach takes the best parts of traditional tabletop methodology and makes it practical for busy, resource-conscious teams:
Scenario:
It’s Monday morning. Employees across the organization can’t access shared files. IT discovers network drives are encrypted and showing ransom demands. Customer service is getting calls about service disruptions. Local media is reporting the outage.
- Phase
-
Immediate response
(first 30 minutes) - Key questions to discuss
-
Who do we notify?
What info do we need?
How do we contain the damage?
What should we tell employees right now?
- Phase
-
Short-term management
(first 24 hours) - Key questions to discuss
-
How do we assess the full impact?
Can any teams keep working?
Do we inform customers?
Do we call law enforcement?
- Phase
-
Recovery planning
(24-72 hours) - Key questions to discuss
-
What systems do we restore first?
Do we trust our backups?
How do we make sure the infection is gone before we go live again?
- Phase
-
Long-term considerations
(weeks/months) - Key questions to discuss
-
How do we prevent this in the future?
What should we change in our playbook?
What will help rebuild trust with customers and employees?
Run it simply but meaningfully, by assigning real roles (CEO, IT, HR, comms), keeping it time-boxed (30–60 minutes max), and documenting takeaways, not performance.
Remember, you don’t need to simulate panic. What you’re really practicing is decision-making, clarity, and alignment under pressure.
End the exercise by assigning one improvement to implement, like policy, a checklist, or a communication template.
Byte-sized tip: Use Secure Practice’s Human risk metrics to spot which teams may need extra support, and tailor follow-up training based on how they responded in the exercise.
And when you’re ready to make these scenarios easier to run—or repeat more often—there’s an even simpler way.
Coming soon: interactive, zero-prep scenarios with PrepJam
PrepJam has long been part of Secure Practice’s privacy-focused human risk management platform, helping people build cybersecurity skills and confidence. Now, it will soon become available in a new interactive format—zero-prep, self-service scenarios you can assign to your team in minutes.
Each scenario walks participants through real-world threats like ransomware, phishing, and business email compromise, using branching storylines, practical decision points, and instant feedback to turn learning into action.
Whether you’re running a tabletop in person or want something teams can do on their own time, PrepJam helps you turn cyber awareness into actual practice:
Self-guided, click-through scenarios that feel like a conversation
Tailored by team or role (e.g., finance, HR, IT)
Trackable engagement with insights built in
Designed for low-prep teams who want high-impact learning moments
It's the collaborative thinking of traditional tabletop exercises, made scalable and accessible for the modern workplace.
Make training stick: measure what matters
Once you’ve tried one or more cybersecurity exercises, don’t stop there.
The real value comes from the reflection, the conversations, the behavior change that happen next. That’s why it’s so important to track engagement, follow up intentionally, and adapt based on what you learn.
Traditional click rates only scratch the surface. To see the true impact of your cybersecurity exercises for employees, look at indicators like behavior change, peer discussion, and improvement over time.
Here are a few smarter metrics that reveal real progress:
| Metric | Why it matters |
|---|---|
| Recognition speed | Are people spotting suspicious elements more quickly over time? |
| Reporting behavior | Do people report phishing attempts or ask before acting? |
| Discussion signals | Are people talking about security topics in Slack or team chats? |
| Improvement trend | Are individuals becoming more resilient across multiple simulations or challenges? |
These signals help you spot who’s developing strong instincts, and who might need more support.
See what’s working, no spreadsheets needed
You don’t need to chase down completions, export CSVs, or beg people to answer surveys. Secure Practice handles this automatically with a dashboard that shows:
Completion rates: who’s engaging with training, without needing manual reminders
Click behavior in phishing: who’s spotting threats, and who’s still at risk
Module-level progress: which security awareness content is effective vs. skipped or repeated
Anonymized team-level trends: which roles or departments may need extra support
Engagement patterns: where people are dropping off or losing interest, and what’s working best
All of this happens behind the scenes—no spreadsheets, no learning management system headaches. Just open the platform and instantly see who’s participating, what content actually lands, and where behavior is improving or slipping.
Secure Practice gives you the tools, the feedback loops, and the visibility to do it right, without creating more work for yourself or your team.
Build real capabilities, not just checkboxes
Cybersecurity exercises help real teams build the confidence, coordination, and reflexes they’ll need when an actual threat comes through the inbox or across the network.
The best programs aren’t the most sophisticated—they’re the most consistent.
The exercises in this guide work because they’re:
Simple to set up, even with a small team
Grounded in how people actually behave at work
Designed to scale with your organization’s maturity
Focused on capability, not just awareness
This approach is grounded in what actually works: giving people the context, confidence, and tools they need to respond well when something feels off. Research like The Missing Link in Email Security and recent findings shared at Black Hat make it clear: training that’s supportive and relevant builds real capability.
Fear and shame don’t create better security habits. Empowerment does. That’s why our approach focuses on realistic challenges, smart follow-up, and tools that adapt to how people really work.
Secure Practice helps you do all of this with less effort and more impact. From phishing simulations and e-learning modules to tabletop exercises and behavioral metrics, it’s a full toolkit for human-focused cybersecurity training.
You don’t need a big budget or in-house experts. Just a few minutes a week, a few good scenarios, and a platform that adapts as your needs evolve.
Want a head start?
Try a free security awareness module or request a tailored human risk report from Secure Practice to see how these exercises could work for your team.
FAQs about cybersecurity exercises
Why is employee cybersecurity training so important for business?
The business case for cybersecurity exercises extends far beyond preventing attacks. Regular training programs can deliver benefits—some of them measurable—that directly impact organizational performance:
Improved decision-making under pressure: teams that rehearse real-world scenarios may make faster, clearer decisions during actual incidents
Fewer human errors: when secure habits are practiced regularly, they’re more likely to become instinctive rather than something people have to recall under stress
Better coordination across departments: exercises can help uncover communication gaps before they turn into security gaps
Regulatory compliance: many industries now require proof of security awareness programs and response readiness
Cost savings: preventing even one major incident can save millions, and exercises are a low-cost, high-impact way to reduce risk
Higher employee confidence and satisfaction: people often feel less anxious and more in control when they know how to recognize and respond to threats
What are cybersecurity tabletop exercises?
Traditional tabletop cybersecurity exercises are discussion-based scenarios where teams gather around a conference table to talk through how they would handle a simulated security incident, without needing to run technical responses in real time.
Modern scenario-based exercises keep this collaborative approach while removing the logistical barriers. Whether conducted as informal team discussions or through interactive digital formats, these exercises are ideal for any organization that wants meaningful training without heavy investment in tools or setup.
They’re also cost-effective, easy to run, and highly adaptable. Common scenarios include ransomware, data breaches, insider threats, and supply chain attacks.
Secure Practice supports both traditional discussion-based exercises and next-generation scenario training through tools like PrepJam, making it even easier to run these with minimal prep while maintaining the collaborative decision-making benefits.
How is PrepJam different to tabletop exercises?
We’ve built PrepJam as the next evolution of tabletop-style training—moving beyond conference room discussions to interactive, scalable cybersecurity exercises you can assign to teams with no setup required.
While traditional tabletop exercises require coordinated scheduling and facilitation, PrepJam delivers the same collaborative decision-making practice through self-guided scenarios that teams can complete on their own time.
Secure Practice supports tabletop-style learning through scenario-based e-learning and tools like PrepJam, launching soon, making it even easier to run these with minimal prep.
How often should organizations run cybersecurity exercises?
The best results come from consistent, layered training:
Monthly: phishing simulations, quick challenges, myth-busting quizzes
Quarterly: role-specific training, tabletop scenarios, behavior-based microlearning
Annually: full org-wide simulations, crisis coordination drills, leadership briefings
Event-triggered: exercises after major incidents, org changes, or new threat intel
The key is consistency. Regular, achievable exercises are more effective than elaborate plans that never get implemented.
Secure Practice makes it easy to maintain this rhythm by automating exercise delivery, adapting content to team needs, and helping you stay on track without chasing people for participation.
Why is cyber security training so important for small businesses?
Small businesses face unique cybersecurity challenges that make regular exercises especially critical for their survival and growth:
Limited staff means general employees need basic security skills, not just the IT lead
Increased targeting: small businesses are seen as easy, high-value targets by attackers
Higher impact: one attack can shut down operations, so prevention is essential
Same compliance standards: many regulations apply regardless of company size
Fewer recovery resources: with no cyber insurance or incident response retainers, training is your safety net
What types of cyber security exercises work best for different team sizes?
Exercise effectiveness depends partly on matching the format to your team size and organizational structure:
Small teams (5–15): tabletop discussions, collaborative phishing analysis, interactive lunch-and-learns
Medium teams (15–50): role-specific simulations, cross-functional drills, peer mentoring, lightweight competition
Large teams (50+): automated phishing simulations, cascading tabletop programs, department-level tracking and metrics
No matter the size, the best exercises are the ones your team actually completes, and that feel relevant to their work.


