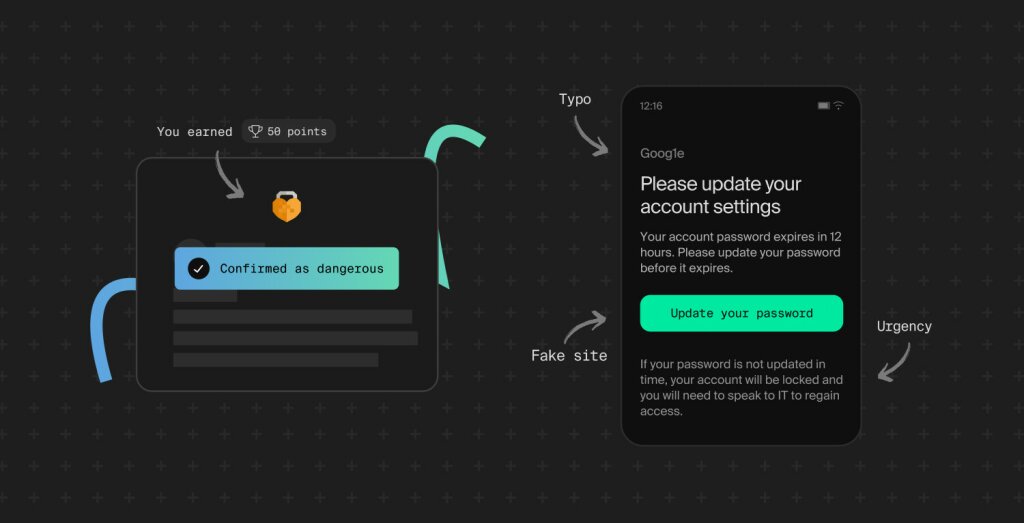
Meanwhile, threats are evolving fast. Social engineering attacks are tailored, convincing, and built to manipulate human behavior, not just exploit technical flaws.
In other words: cyber threats are getting more personal, more persuasive, and more human.
So if we want security training to keep up, we need to rethink how we approach it. Less like auditors handing down rules, and more like marketers earning attention and building trust.
So what can security teams learn from marketers? A lot more than you’d think. Let’s dive in.
Why effective security training needs a marketing mindset
Because marketing teams have cracked the code on something cybersecurity desperately needs: how to make people care.
They know how to:
Speak to what people value
Simplify complex ideas
Inspire action, not just awareness
By borrowing their playbook, you can make cyber skills not just memorable, but meaningful.
When we apply these three lessons of good marketing—audience segmentation, storytelling, and journey design—we turn security training into something people remember, act on, and even champion.
1. Understand the power of audience segmentation
Most security training treats people as one big group, with the same lessons, tone, and expectations. But marketers know better: no single message works for everyone.
So they use audience segmentation.
What marketers do
Marketing teams have cracked a critical insight: relevance drives engagement. Studies in marketing psychology consistently show that personalized messaging can improve engagement rates by 20-30% compared to generic communications.
When messages feel personally relevant, people lean in. When they don't, people check out entirely.
How marketers think about different people
They segment by behavior, not just demographics: What matters isn't job title—it's how people actually behave. Do they engage with content or ignore it? Ask questions or stay silent? Seem confident or overwhelmed?
They consider learning preferences and motivational factors: Some people are motivated by avoiding problems, others by achieving recognition. Some want detailed explanations, others just the bottom line.
They pay attention to context: The same person might be receptive to learning at 10 AM on Tuesday but completely checked out at 4 PM on Friday. Marketers think about when, where, and how people are most likely to pay attention.
What security teams can learn
Forget the traditional approach of segmenting by department or seniority. The most effective cybersecurity segmentation focuses on how people actually behave around security—and why.
Do they report phishing or ignore it? Are they cautious or overly confident? Do they engage with training or avoid it?
Segmenting based on these user behavior and awareness levels helps you deliver the right message to the right person, at the right time. And it works.
One peer-reviewed study from 2025 found that when training was tailored to how people actually behaved—not just their job title—it led to 47% fewer clicks on phishing links and a 58% boost in accurate reports.
By focusing on real behaviors rather than assumptions tied to job titles, security teams can create training experiences that feel personal, relevant, and, most importantly, work. This approach helps people learn in ways that feel relevant to them.
How Secure Practice helps
With MailRisk, you already have insight into how your colleagues engage with real and simulated phishing. It reveals behavioral patterns that help you understand how different people think about security:
Response time patterns: Advocates tend to analyze suspicious emails carefully before reporting them. Anxious learners might report quickly but often flag legitimate emails. Resistant individuals either ignore suspicious emails entirely or click immediately.
Learning trajectory: You can see who improves over time, who plateaus, and who seems to get worse. This helps you identify when someone might be moving between segments and needs a different approach.
Question and feedback patterns: The questions people ask (or don't ask) reveal a lot about their comfort level and understanding. Advocates ask strategic questions about emerging threats. Anxious learners ask clarifying questions about basic concepts. Resistant individuals rarely ask questions at all.
Use this data to create natural segments and adapt your communication. For example:
5 behavioral patterns that actually predict security outcomes
Advocates
Natural security champions who go beyond compliance.
- What they do
-
Report threats quickly and accurately, engage deeply with training, mentor others.
- What they need
-
Advanced threat intel, recognition, opportunities to lead or co-create training.
- How to communicate with them
-
Treat them as partners.
Involve them in improving training and share the “why” behind security updates.
- Example message
-
“Thanks for being a security champion. Here's some advanced threat intelligence that might interest you. We'd love your thoughts on how to help the rest of the team spot these trends.”
Willing but overwhelmed
Want to do well, but feel stretched thin.
- What they do
-
Inconsistent performance, partial training completions, effort varies with stress.
- What they need
-
Bite-sized guidance, small wins, reassurance that every effort helps.
- How to communicate with them
-
Be supportive and efficient.
Keep comms short and motivational, respect their time, acknowledge constraints.
- Example message
-
"We know you're juggling a lot. Here's a quick 2-minute guide to spotting the most common phishing attempts. No need to memorize everything—just bookmark this for when you need it."
Anxious learners
Feel insecure or intimidated by security tasks.
- What they do
-
Over-reporting, avoidance of training, frequent questions when they do engage.
- What they need
-
Emotional safety, simple visuals, permission to ask questions and fail safely.
- How to communicate with them
-
Use kind, plain language.
Emphasize learning over perfection. Offer visual aids and step-by-step instructions.
- Example message
-
"Lots of people find phishing emails tricky—that's exactly why scammers make them so convincing. Here's a simple checklist you can follow when you're unsure about an email. Remember, it's always okay to ask for help."
Resistant or disengaged
Don’t see security as their problem—or reject the process entirely.
- What they do
-
Click through training without care, ignore protocols, exhibit risky behaviors.
- What they need
-
Clear relevance, relatable stories, social proof that security matters to peers.
- How to communicate with them
-
Lead with emotion and real stories.
Use peer validation. Make it personal and relatable.
- Example message
-
"Your colleague Sarah in Accounting caught a fraudulent invoice last week that could have cost us $15,000. She says the thing that tipped her off was [specific detail]. Here's what to watch for in your own work."
Evolving participants
In transition—starting to engage more and showing signs of progress.
- What they do
-
Show increasing interest in training, begin reporting incidents, start asking better questions.
- What they need
-
Encouragement, tailored next steps, recognition of growth.
- How to communicate with them
-
Reinforce progress.
Use “You’re improving!” messages. Offer personalized suggestions for their next learning step.
- Example message
-
"You’ve made great progress over the last few months—your attention to detail in the latest phishing simulation really stood out. Here's a next-level challenge you might enjoy."
Just like marketing, segmentation in security training makes your message more likely to land, resonate, and drive the behavior change you’re aiming for.
You’re giving people exactly what they need to improve, based on how they behave, not just where they sit in the org chart.
With Secure Practice, you can fine-tune this even further:
Proactive reporters, like your Advocates or Evolving participants, can be challenged with advanced phishing simulations and recognized through gamified achievements in the learning portal. This keeps motivation high and encourages deeper skill-building.
Anxious learners who trigger frequent false alarms are easy to spot with MailRisk activity logs. Use this insight to deliver bite-sized visual tips and supportive feedback messages that build confidence without overwhelming them.
The Resistant group, where engagement is low, might not respond to standard content. Here, Secure Practice’s customizable micro-training and story-based modules allow you to shift the tone—embedding real-life scenarios or peer-driven testimonials that bring the message home in a more personal, persuasive way.
2. Harness the art of storytelling
It was a Tuesday afternoon when Marcus, a project manager at a growing tech startup, almost lost his company $2.3 million.
The email looked perfectly legitimate. It appeared to come from their biggest client, requesting an urgent wire transfer. The sender's email address was one character off from their actual client contact, but Marcus was rushing and didn't notice.
Something made him pause though—the slightly formal tone didn't quite match how Sarah usually communicated. Instead of forwarding it to Finance, he picked up the phone and called Sarah directly.
"Wire transfer?" she sounded confused. "We haven't requested any payments." That one phone call saved the company from devastating loss.
Instead of just sending a company-wide warning email, the security team asked Marcus to tell his story at the next all-hands meeting.
The response was immediate. People started sharing their own stories and asking thoughtful questions. That one story session led to a 40% increase in suspicious email reports over the next three months, and the reports weren't random—they were thoughtful and accurate.
This hypothetical situation matches up with what marketers know works: storytelling. Research backs it up: a recent study published in the Quarterly Journal of Economics found that when people read a story, they remember it more than twice as well as when they’re just given the same information in statistical form.
You can list the signs of a phishing email all day. But if someone doesn’t understand why it matters—or how it plays out in real life—they’ll tune out. Storytelling changes that.
What marketers do
Marketers don't lead with product specifications; they tell stories about how their products solve real problems.
Think about memorable ads: the insurance commercial about the family protected during a storm, the car ad showing confident navigation through challenges, the software demo following someone's daily routine. They explain benefits and show consequences.
Marketers use stories to make abstract benefits feel concrete and personal. When you feel something while hearing a story, you remember both the emotion and the message long after the details fade.
What security teams can learn
Show people what cyber threats look like in their world, not just abstract rules.
Tell the story of how a convincing invoice scam almost got through Finance. Walk through how a quick click on a fake calendar invite led to days of system recovery. Show what it feels like to navigate that moment when something seems legitimate but feels off.
Cybersecurity storytelling works across experience levels: it makes abstract threats real for newcomers, creates context for experienced users, and shows skeptical audiences that security affects real people doing real work.
How Secure Practice helps
Stories are powerful, but interactive stories are transformative. Instead of just hearing about Marcus's decision-making process, what if people could step into his shoes and make the choices themselves?
Cybersecurity exercises turn stories into something people can interact with. They’re the basis of our human-centric cybersecurity approach.
Use Secure Practice to build breach simulations with branching paths, internal characters, and real decision points. Here’s an example:
Branching narrative exercise: business email compromise simulation
| Choice | Result | Learning moment |
|---|---|---|
| Forward to Finance immediately | Finance processes the payment; $2.3M loss discovered three days later | "This is exactly how 43% of business email compromise attacks succeed. Let's look at what could have prevented this." |
| Call the client to verify the request | Client confirms they never sent the email; potential attack prevented | "Excellent verification! This simple step is the most effective defense against BEC attacks." |
| Report the email to the security team | Security investigates and discovers it's part of a broader phishing campaign targeting multiple employees | "Great catch! Your report helped protect the entire organization." |
Using behavioral data from MailRisk, you can customize story scenarios:
For security champions: complex, multi-layered scenarios that require advanced threat detection skills
For anxious learners: supportive narratives that emphasize that uncertainty is normal and verification is always acceptable
For overwhelmed colleagues: quick, clear scenarios that focus on the most common threats they're likely to encounter
For resistant individuals: peer-focused stories featuring colleagues in similar roles making good security decisions
With this interactive exercise, instead of just reading about a phishing attack, colleagues step into the role of the target. They make choices, experience the fallout, and learn what could’ve gone differently.
3. Nurture behavior change like a customer journey
Behavior change doesn’t happen all at once. And it definitely doesn’t happen after a single training session.
If we want people to build lasting cybersecurity habits, we need to guide them, step by step, over time.
What marketers do
Marketers map customer journeys through predictable stages: awareness, consideration, and decision-making. They deliver the right message at the right time, like a helpful email, reminder, or how-to guide tailored to each stage.
Marketers also understand that people move through these stages at different speeds. Some customers are ready to buy after a few touchpoints, while others need months of nurturing. They design systems that accommodate both fast-movers and slow-adopters.
Most importantly, marketers know that the journey doesn't end with the first purchase. They continue nurturing customers to build loyalty, encourage repeat purchases, and turn satisfied customers into advocates who influence others.
What security teams can learn
Security awareness should follow a similar path. Instead of cramming everything into one annual module, build a rhythm.
Design touch-point sequences that build knowledge and confidence over time:
Start with basic awareness: light content like quick videos or tip-of-the-week messages about the most common threats people actually encounter
Add hands-on practice: follow up with short quizzes or interactive challenges in safe environments
Introduce more complex scenarios: gradually add more advanced simulations and decision-making scenarios
Meet people where they are. Someone who’s just learning to spot phishing shouldn’t be thrown into a high-stakes simulation. And someone who’s clearly engaged shouldn’t be stuck repeating basics.
Your system should accommodate both without making anyone feel left behind or held back.
How Secure Practice helps
You can build out this journey using Secure Practice tools using behavioral data to guide people along personalized learning paths.
Start with light-touch content, layer in quizzes or behavior nudges, and use behavioral insights to adjust along the way. The timeframe for this journey can vary, depending on how your training goes, but here’s a look at what you could expect:
- Stage
-
Awareness and relevance
(typically 2-6 weeks)
- Goal
-
Help people understand how cybersecurity fits into their daily work and why it matters to them.
- Content approach
-
Real stories tied to role-specific risks
Simple explanations of common threats
Bite-sized tips that feel immediately useful
Framing security as protecting what matters to them
- Touchpoints
-
Welcome nudges via MailRisk
Weekly “threat spotlight” campaigns
Short in-platform videos or story-based nudges
Visual risk snapshots from Human Risk Metrics
- Success indicators
-
Recognizing threats in context
Basic engagement via clicks or opens
First signs of awareness in MailRisk behavior
- Stage
-
Basic skill building
(typically 1-3 months)
- Goal
-
Build fundamental security instincts and encourage low-friction practice.
- Content approach
-
Interactive simulations with feedback
Clear “how-to” on verifying suspicious activity
Recognizing common red flags
Boosting early confidence
- Touchpoints
-
Simulated phishing with guided feedback
Gamified e-learning modules
Quick quizzes or Slack nudges
Peer highlights in monthly comms
- Success indicators
-
Fewer risky clicks overall
Higher reporting rates
Increased completion of training modules
- Stage
-
Confidence and judgment
(typically 3-6 months)
- Goal
-
Strengthen advanced recognition skills and reinforce good judgment under pressure.
- Content approach
-
Complex, realistic phishing simulations
Situational practice using branching storylines
Decision-making challenges under stress
Team collaboration
- Touchpoints
-
Multi-path simulations in phishing training
Advanced breach scenario exercises
Cross-department leaderboard results
- Success indicators
-
Employees spot advanced threats
Improvement in human risk metrics
Peer-to-peer support emerging
- Stage
-
Advocacy and continuous learning
(ongoing)
- Goal
-
Cultivate internal advocates who promote security culture and contribute to learning.
- Content approach
-
Real-time threat intelligence updates
Recognition and professional growth
Opportunities to mentor others
Involvement in awareness program building
- Touchpoints
-
Quarterly reports shared with champions
Invite advocates to co-create content
Early access to new Secure Practice features
Integration with internal awards/comms
- Success indicators
-
User-generated stories and testimonials
Advocates leading by example
Increased voluntary participation and engagement
The platform's human risk metrics help you track progress over time and identify when colleagues might be ready to move to the next stage of their security awareness journey.
If someone’s clearly progressing, give them more challenges. If they’re disengaged, change the format or tone. The idea is to support the habit, not just complete a task.
And like marketing funnels, this kind of approach works best when it’s ongoing—not one-and-done.

Cyber security hands-on training works best when it earns attention
Marketers have long understood that if you want to influence behavior, you first have to earn attention and make it personal. Security training should do the same.
With hands-on training platforms like Secure Practice, it’s now easier than ever to put these ideas into action. You can build interactive, context-rich experiences that meet people where they are—and turn security from a burden into a skill they feel confident using.
Secure Practice makes it easy to measure and scale what works
From phishing simulations to human risk insights and gamified training, our platform helps you transform awareness into real action. Build a smarter, more resilient organization—without guesswork.
Security meets marketing: 6 common questions and answers
Why should cybersecurity professionals study marketing?
Because the core job of a security awareness professional is to influence behavior, just like a marketer. Marketing strategies help us speak more clearly, build trust faster, and engage people in ways that actually stick.
Can storytelling really make a difference in security training?
Yes. People remember stories far more than they remember lists or instructions. A relatable scenario makes a threat feel real, and a resolution gives them something to model.
This isn’t just about better content. It’s about communication lessons for cyber teams, rooted in psychology, persuasion, and real-world experience. It’s about applying marketing psychology to cyber training, and designing cyber awareness campaigns that make people want to learn.
Effective security storytelling transforms not just how people learn about threats, but how they think about their role in organizational security:
How do we help people recognize threats they've never encountered before?
What's the most effective way to communicate complex security concepts without overwhelming people?
How can we make security training feel relevant to people's actual work experiences?
What techniques help people remember security lessons during high-pressure situations?
How do we build security intuition, not just security knowledge?
What methods help people develop confidence in their security decision-making?
How can we create security awareness that spreads organically throughout the organization?
What storytelling approaches work for people who resist traditional training?
How do hands-on simulations relate to marketing?
Just like marketers use product demos to let people experience value, security teams can use simulations to help employees practice real-world decisions in a safe environment. Experience builds confidence.
This kind of practical cyber security skills development is what helps build real-world readiness.
What is segmentation in the context of cyber training?
Segmentation supports both internal communications in security and security awareness communication strategies.
It means adapting your training based on how people behave, not just what department they’re in.
When you implement thoughtful audience segmentation, you can finally answer the questions that keep security professionals up at night:
Why do some people consistently make good security decisions while others struggle?
How can we reduce training time while actually improving security outcomes?
What's the most effective way to communicate with people who seem resistant to security guidance?
How do we measure whether our training is actually making people more secure?
Which employees are ready to take on security champion roles?
How can we turn our natural advocates into effective peer educators?
What predicts whether someone will improve their security behavior over time?
How do we balance efficiency with personalization in security communications?
How can I start applying these ideas in my organization?
Start small. Segment your audience for the next phishing campaign. Reword one feedback message to sound more human. Share one success story from a peer. Every change that makes security feel more personal is a step in the right direction.