It’s a familiar story for many executives: a busy day, a flood of messages, and one that looks just credible enough to slip through.
The sender seems urgent, the timing feels right, and before you know it, you’ve acted.
Every CEO phishing attack reveals something that could save your organization thousands in breach costs (and it has nothing to do with more training). Keep reading to understand how.
The perfect storm for human error
CEO phishing fraud works because it exploits how our brains operate under pressure.
Even leaders in cybersecurity are vulnerable. They spend their days discussing security culture, reviewing awareness programs, and teaching others how to spot scams. Yet one afternoon, between back-to-back meetings, a convincing email slips through. It looks urgent. It references a real project. And for a moment—just long enough—it feels real.
Attackers rely on social engineering techniques, creating a false sense of urgency. They use public information—meetings, absences, project announcements—to craft messages that feel authentic, fit neatly into someone’s day, and bypass the natural hesitation that keeps us safe.
Then they rely on psychology to do the rest.
As psychologist Daniel Kahneman explains, our brains have two modes of thinking:
System 1, fast and intuitive, perfect for making routine decisions
System 2, slow and deliberate, essential for analysis, but energy-intensive
When we’re rushing, System 1 takes over. It helps us stay efficient, but it also skips steps.
That’s why a well-crafted phishing email can feel perfectly legitimate, even to someone who spends their career warning others about such attacks.

The phishing awareness training trap: why current approaches fail
Most security training assumes people will stop and think critically under pressure. Yet research shows this is unrealistic.
Sophisticated attacks, like the ones targeting CEOs, are designed to bypass the obvious red flags—spelling mistakes, generic greetings, or urgent password requests—that traditional programs teach people to watch for. In other words, these trainings often focus on artificial scenarios that don’t match how real attacks actually unfold.
We’re teaching people to spot signals that skilled attackers purposely avoid, while overlooking the psychological and situational factors that truly make people vulnerable.
When someone is juggling meetings, deadlines, or unexpected problems, their brain defaults to quick, automatic responses. Expecting perfect vigilance in those moments sets people up to fail.
This false sense of control is common in security teams too, as our own CEO once reflected:
We who work in IT and security can easily get the feeling of being superheroes when facing everyday scam attempts. A bit like doctors on TV who never get sick, no matter how contagious the environment becomes. How wrong we can be!
– Erlend Andreas Gjære, CEO and Co-founder at Secure Practice
What actually works: building with human nature
You can't train people out of being human, but you can build systems that work with psychology instead of against it.
In real life, phishing attempts don’t arrive during workshops or in quiet moments. They hit when your attention is already thin: between calls, before a deadline, or on a Friday afternoon.
That’s the gap between knowing and doing. And it’s where organizations need to focus next: creating a support system that helps people check their instincts before taking action.
The goal isn’t to eliminate human error; it’s to make safe actions effortless and mistakes recoverable.
To do that, email security systems need to:
Work in real-time when people are stressed
Guide without requiring perfect memory of training
Analyze threats while people focus on their actual work
Offer clear next steps rather than vague warnings
Instead of expecting perfect threat analysis under pressure, organizations need tools that act like having a cybersecurity expert looking over your shoulder—quietly analyzing suspicious emails and providing clear guidance when you need it most.
This is exactly the approach behind MailRisk: a tool that helps people check suspicious emails in real time.
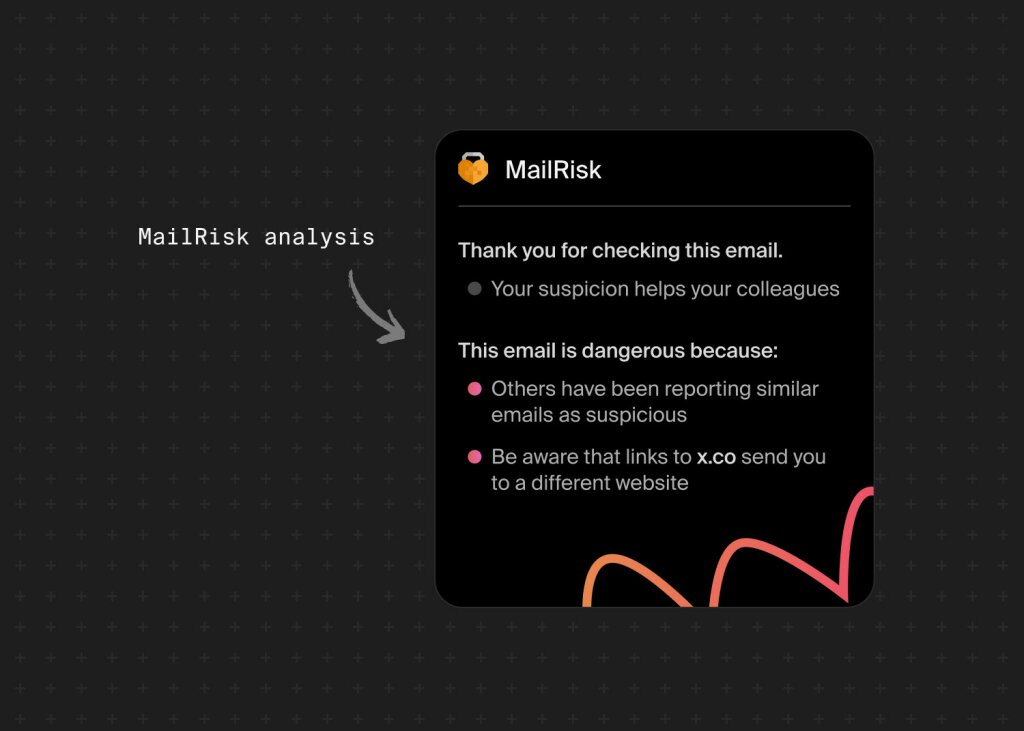
The MailRisk approach: getting help when you need it
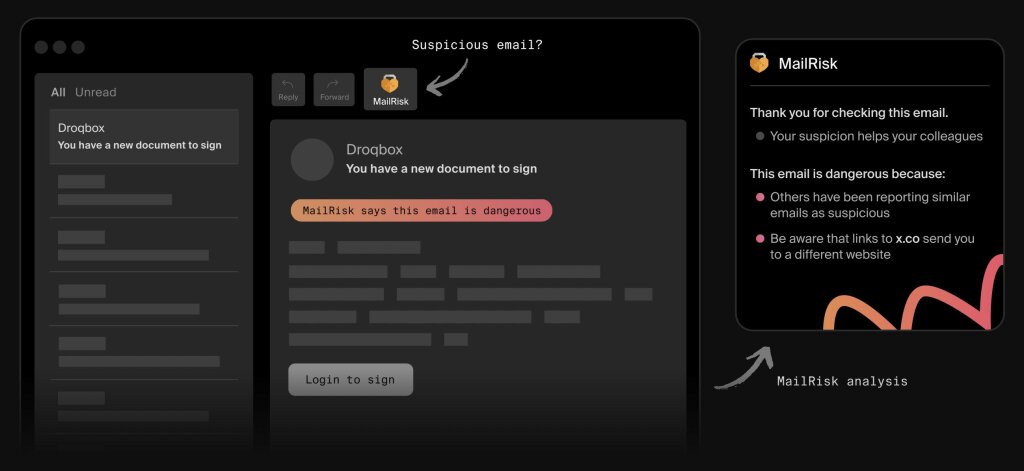
MailRisk integrates seamlessly into existing email workflows through a simple toolbar button in Outlook and Gmail. Unlike other basic reporting buttons, MailRisk is designed to help you check suspicious emails before you act on them.
When someone encounters a suspicious message and clicks the MailRisk button, they’re not just reporting an incident, but asking for help: “Can you help me figure out if this is safe?”
MailRisk also enables phishing simulations—exercises that mirror real workdays in tone, timing, and urgency.
These simulations don’t aim to “catch” people off guard. Instead, they demonstrate how easily pressure and context affect judgment. Each simulation becomes a safe, guided opportunity to learn through experience, supported by real analysis and immediate feedback.
Behind every click of the MailRisk button sits an entire analysis process designed to give instant clarity and confidence:
Real-time threat intelligence checks the message against crowdsourced data from other organizations
Behavioral analysis compares it with the sender’s usual communication patterns using EU-based machine learning
Psychological detection identifies manipulation tactics: tone, timing, and emotional triggers that prey on human decision-making
Clear guidance tells the user exactly what to do next: is it safe, or should they verify it through another channel?
Expert backup ensures that when the system can’t decide, a human analyst can
Want to see how this works behind the scenes? Our complete MailRisk guide walks through the analysis process step-by-step.
Why this matters for your organization
When a phishing simulation catches a CEO off guard, it’s not proof of failure—it’s proof that traditional “gotcha” training misses the point.
Critics note that many phishing programs still rely on repetitive testing and punishment, even though people continue to get caught. If even experienced professionals can fall for a simulated attack, then clearly the answer isn’t just more of the same.
The real question isn’t whether people will ever fall for phishing. They will. The question is how your organization responds when it happens.
We’ve seen this exact pattern in one of our own internal phishing simulations. It only takes one rushed moment for even a security-minded leader to hesitate or click. That experience shaped how we think about awareness today: less about testing people, more about supporting them when it matters.
What organizations need is defense in depth: a layered approach where human awareness is reinforced by technical safeguards, supported by a strong security awareness conversation that encourages colleagues to report mistakes and learn from them.
I'm often told that those of us who work in security and identity never become victims of phishing. Which is obviously completely wrong. Anyone can become a victim of this.
– John Erik Setsaas, Digital Identity Expert & International Speaker
Instead of reprimanding people or doubling down on harder tests, build awareness programs that:
Avoid punitive responses: treat clicks as learning opportunities, not grounds for blame. Employees will only engage if they know they won’t be shamed for getting tricked.
Reframe awareness efforts: move away from one-off drills that measure failure rates. Focus instead on creating a culture where people feel safe to raise a flag when something looks suspicious.
Invest in support systems: tools like MailRisk help employees act safely in the moment, by making it easy to report uncertainty without slowing down their work. This shifts the burden from individual perfection to collective defense.
Because in the end, security isn’t based on flawless human performance, but building systems that support people when their attention, memory, or judgment is stretched thin.
That means responding with support, not shame, and giving people clear ways to recover from mistakes and keep learning.
Even security professionals have close calls. Secure Practice CEO, Erlend Andreas Gjære once shared his own “near-miss” story about almost falling for a phishing attempt—a reminder that awareness isn’t about being perfect, but about catching ourselves in time to learn and improve.
Ready to move beyond traditional phishing training?
MailRisk is a the real-time email analysis tool built by security researchers to work with human psychology, and help people stay safe even when focus slips.
FAQs about email security
What are typical signs of a CEO impersonation phishing attempt?
High-level executives and company leaders can also be impersonated by cybercriminals, in an effort to manipulate victims from other departments.
Finance departments are prime targets for these CEO fraud attacks, also called business email compromise (BEC). Unlike malware or ransomware, BEC doesn’t need to break into your systems—it tricks people instead.
Look out for red flags: an unusual sense of urgency, a phone call from unknown numbers, or instructions demanding immediate action around sensitive data or confidential information.
Fraudsters often ask for a wire transfer to a different bank account, tricking the CFO into releasing funds.
What phishing techniques are used to target CEOs or CFOs?
Whaling is a targeted form of phishing that focuses on high-level executives. These attacks are increasingly common against high-profile industries such as healthcare and finance, where confidential data and large transactions are involved
Scammers may use a spear phishing attack to impersonate company executives or spoof a trusted domain name to pressure staff into transferring money or sharing sensitive information.
What are the most common methods of a CEO fraud attack?
Cybercriminals and fraudsters often research their targets on LinkedIn and other social media platforms to impersonate company executives.
They combine these details with spoofing, fake emails, or even phone calls to manipulate employees into disclosing confidential data or making unauthorized wire transfers.
What should I do if I'm unsure about an email I received?
Use a tool like MailRisk to check it before taking action. Getting help when you're uncertain is much more effective than trying to remember training guidelines while under pressure.
Mature security cultures encourage employees to report suspicious messages, whether they look like phishing emails, spoofed email domains, or other forms of phishing scams, rather than guessing.
How can I avoid clicking phishing emails when I'm traveling or stressed?
Rather than relying on perfect vigilance during high-stress periods, use tools that can help you check suspicious emails in real-time.
The most effective approach combines immediate access to expert guidance with organizational cultures that celebrate asking for help when uncertain.
This reduces vulnerabilities to cyberattacks such as spear phishing or ransomware delivered via email.
What makes MailRisk different from traditional email security tools?
While most providers offer basic reporting functionality or email filters, MailRisk focuses on helping you understand suspicious emails before you act on them.
Instead of just sending fake emails away for later analysis, MailRisk provides immediate context, highlights red flags, and explains common social engineering techniques that cybercriminals and scammers use.
Why do even cybersecurity experts fall for phishing?
Cybercrime doesn’t discriminate, and context, timing, and psychological pressure affect everyone equally.
The right mix of social engineering tactics and a sense of urgency can override even strong security awareness training.
In the end, everyone benefits from tools that help them double-check their instincts when something feels suspicious.
How should organizations respond when employees click phishing emails?
Treat mistakes as learning opportunities, not reasons to blame. A supportive culture, system improvements, and accessible verification tools help reduce repeat errors and strengthen security overall.
When colleagues feel safe reporting phishing attacks or spoofing attempts, organizations can detect cyber threats faster and avoid costly data breaches.
How can businesses protect themselves from CEO phishing attacks?
Email filters block many fake emails, but not all. Strong email authentication methods like SPF, DKIM, and DMARC, combined with multi-factor authentication, help prevent spoofed accounts from reaching employees.
At the same time, phishing scams rely on social engineering—something only people can catch. Ongoing security awareness training keeps employees alert to red flags like urgent wire transfer requests or emails impersonating executives. Tools like MailRisk reinforce that training in real time, giving staff instant guidance when they’re unsure.
This combination of strong controls, recurrent training, and real-time support is what stops phishing scams from turning into costly financial losses.