Managing human risk isn’t about playing the role of the cyber police or throwing technical terms and fear tactics at your colleagues. It's about understanding that people are the heart of every security strategy—real, busy, and sometimes overwhelmed people.
Human Risk Management (HRM) integrates these human factors into your broader cybersecurity strategy in a way that sticks. Instead of viewing your team as a liability, HRM helps you see them as an integral part of your defense system, creating a culture where security is a natural part of everyday operations, not a once-a-year training session everyone dreads.
Here’s how to do that effectively without losing your sanity, or worse, your team’s trust and engagement.
1. Get leadership to practice what you preach
Start at the top. If leadership isn’t convinced that human factors are crucial to security, your efforts will fall flat. Show them why it matters—how a well-informed team can be the difference between a minor hiccup and a full-blown crisis.
Explain it in terms they understand: less downtime, fewer breaches, and ultimately, more trust from clients and customers. Remember, influencing leadership is about translating tech needs into business benefits.
You’re more effective in getting what needs to be done when you’re able to influence others. To influence, you need to make sure people who don’t understand technical subjects understand why you need the budget to do it.
How to do it: propose a leadership briefing that links HRM to real-world outcomes. Use simple examples, like how better email security led to more reported incidents related to suspicious emails and fewer clicks on malicious links over time.
It is exciting to see the puzzle coming together. Email is in one way very simple, yet a complex attack vector against which we need to protect an entire organization. We cannot think about technical solutions and people separately - both need to be aligned.
2. Make Human Risk Management a part of everyday operations
Don’t let security be that thing everyone talks about only during quarterly reviews. Mention cybersecurity in the company newsletter, include quick tips in team meetings, and make it a part of daily conversations. When it’s woven into the fabric of everyday work life, it becomes familiar and practical.
How to do it: build a strong security foundation that empowers your colleagues, instead of intimidating them:
Start small. Add a “Security Tip of the Week” to your company newsletter or Slack channel. Make it relatable, like how to spot phishing emails or why updating software matters. You can also make it fun, by using memes and other visuals, matching the style of what your colleagues find entertaining online.
Translate tech to non-tech people. The gap between technical and non-technical folks is real, and it’s your job to bridge it. Avoid jargon and focus on explaining the “why” behind security measures. Instead of just saying "we need to encrypt our data," explain it as: "Encryption is like putting your documents into a locked box. Only those with the right key can open and read the contents." When people understand the risks in plain language, they’re more likely to follow through.
Provide balanced cybersecurity education. Education is key, but don’t overdo it. Think of your training like a balanced diet plate: it’s about variety and moderation. Just as you wouldn’t eat the same meal every day, avoid making everyone repeat the same cybersecurity course over and over. Instead, tailor your training to what's relevant for different roles and keep it engaging. Offer detailed, in-depth training to teams managing sensitive data—like adding extra protein to their plate for a boost. Meanwhile, provide lighter, more general training for other roles, akin to a balanced mix of vegetables and grains.
Treat people as your front line. Encourage a “see something, say something” policy where everyone feels safe admitting they’ve made a mistake, like clicking on a suspicious link. Someone from HR that clicks on a link and then notices a strange attachment being downloaded can flag it immediately through an easy-to-use reporting tool or designated contact person. The sooner it's reported, the quicker IT can address the issue, preventing further damage.
Empower through positive reinforcement. People are more likely to follow best practices when they feel appreciated, not micromanaged. For instance, recognize and reward employees who consistently spot and report phishing attempts or follow security protocols. A good security training program should leave your colleagues feeling like they’re part of something important, not just checking a box.
Minimize the cultural potential for mistakes. In fact, if your team is constantly juggling too many priorities, they’re more likely to miss whaling emails or tailgating strangers in the building. Worse, they may not care. Create a work environment where they can focus on what’s important without feeling overwhelmed by regularly reviewing workloads and deadlines to ensure they’re manageable.
Measure and improve. You can’t manage what you don’t measure. Quantifying human-related cybersecurity risks allows you to detect risky behaviors and address them effectively. Regularly evaluate your human risk metrics and adapt your training and policies accordingly. For example, you can track metrics such as the frequency of reported phishing attempts, patterns in password reset requests, and engagement levels with security training modules (or have Secure Practice discreetly do it for you).
Use clear, empathetic language. When rolling out new security protocols, frame them as tools to help the team succeed rather than burdens to bear. You’re there to empower and educate, not to confuse or intimidate. Here’s what that can look like:
Demonizing cybersecurity threats
- Common misconception
-
“Cyber threats always come from hackers trying to cause trouble.”
- The truth behind it
-
“Many threats come from simple mistakes or weak spots, not just malicious hackers. Understanding this helps us focus on real solutions.”
- Why this matters
-
Knowing threats can come from various sources helps us address them more effectively.
Using scare tactics
- Common misconception
-
“If you don’t follow every protocol, you’ll cause a major breach!”
- The truth behind it
-
“It’s more about understanding why each rule is important. Knowing this helps everyone stay cautious without feeling scared.”
- Why this matters
-
Emphasizing the importance of rules helps people follow them without creating fear.
Blaming users for security issues
- Common misconception
-
“The reason for breaches is always user error; people just don’t follow the rules.”
- The truth behind it
-
“Mistakes happen, but we also need to make our systems easier to use. It’s about finding solutions together, not blaming individuals.”
- Why this matters
-
Addressing the root causes of mistakes and improving systems together encourages a collaborative effort rather than assigning blame.
Shaming colleagues for mistakes
- Common misconception
-
“Humans are the biggest threat to cybersecurity because they keep making mistakes.”
- The truth behind it
-
“It’s not just that people make mistakes—it’s that our instinct to find shortcuts often leads us into danger. By addressing these shortcuts, we can make our systems smarter and our training more effective.”
- Why this matters
-
This approach acknowledges human error but highlights the need to refine systems and training to better align with natural human tendencies.
Underestimating the impact of small threats
- Common misconception
-
“Small security breaches are not a big deal compared to major attacks.”
- The truth behind it
-
“Small breaches are like small cracks in a dam—left unchecked, they can grow into major disasters. Treating every incident with seriousness helps prevent larger catastrophes down the line.”
- Why this matters
-
Stresses the importance of addressing all incidents promptly to prevent them from escalating into more severe problems.
3. Partner, don’t police
Nobody likes to be caught in a “gotcha” moment, especially when it comes to security. Gamification, on the other hand, can be a fun and effective way to engage your colleagues in cybersecurity practices—over 80% of people say so.
Different departments within your organization compete to see who has the sharpest cyber awareness. Not only does this foster a sense of camaraderie, but it also makes learning about security an engaging and positive experience.
How to do it: partnering with your colleagues makes security a shared responsibility rather than a dreaded obligation. Instead of setting traps to catch employees off guard, consider a more collaborative approach:
Periodic “live” attack simulation and training exercises. People learn better from mistakes than from theory. These interactive cybersecurity exercises mimic real-time attacks, allowing employees to experience the complexities of a cyber threat as it unfolds. For example, a finance team might face a simulated ransomware attack, while HR might handle a business email compromise attempt. From the initial breach to detection, response, and remediation, teams get to practice being defenders in a controlled, yet realistic environment.
Customize training for contexts and roles. One-size-fits-all training doesn’t cut it anymore. Different groups within your organization face different risks, and your training should reflect that. Create role-specific training sessions that address the unique risks associated with each department (something Secure Practice does for you.) This could involve different scenarios, types of attacks, and response strategies, making sure that everyone is prepared for the threats most relevant to them.
Motivate through variety and challenge. Let’s face it—security training can get repetitive, and 91% of people don’t think it keeps up with the times. To keep it fresh and engaging, plan events that progressively challenge your team, ensuring they are up-to-date, contextualized, immersive, and short. Introduce quarterly “security challenges” that get progressively harder. Start with simple phishing tests, then move on to more complex scenarios like social engineering or multi-vector attacks. Offer small incentives for completing each level successfully to keep the motivation high.
4. Use tools that help (without making your life harder)
Using the right tools can transform your security culture and make HRM not just manageable but effective. We’re talking about tech that actually makes your life easier—not more complicated.
Here are three types of tools you should consider, and how they can make a real difference:
Reporting tools with a full feedback loop: these tools simulate phishing attacks to test your team’s ability to recognize and handle suspicious emails. Tools like MailRisk that integrate directly into your email platform are fantastic for this. It’s like turning your daily emails into a training session that’s both useful and rewarding. Your colleagues can report suspicious emails with just a click, and they get immediate feedback. So, if someone gets a sketchy email, they flag it, and MailRisk does the heavy lifting—analyzing the threat and letting the user know how well they’ve done.
Behavioral analytics tools: these tools track and analyze user behavior to spot any unusual activity that could signal a security threat. They give you an extra pair of eyes on sensitive data and actions. Tools like Sumo Logic can monitor for red flags, like if someone suddenly starts downloading a bunch of sensitive files or logging in from unusual locations. If anything seems off, you get an alert. This way, you can catch potential issues before they turn into full-blown problems.
Security awareness and engagement tools: These tools are all about turning security training into something engaging and interactive. They make learning about cybersecurity less of a chore and more of an experience. Secure Practice offers interactive modules that turn cybersecurity into a game-like experience; from interactive exercises that let your team tackle simulated cyberattacks together to bite-sized lessons and tailored content. We turn those dry training sessions into dynamic, interactive experiences that build team spirit and sharpen skills. Plus, Secure Practice is 100% private and anonymous, so it doesn't create more data protection and privacy issues when you add it to the company's software stack.
Byte-sized tip: supercharge your risk management with the entire Secure Practice toolkit.
For optimal human risk management, use a range of tools—each with unique strengths—to address different security needs. The real magic happens when these tools work together:
Start by using MailRisk data alongside your phishing simulations and threat hunting. This combo gives you a clearer picture of potential threats and helps you zero in on specific risk areas.
For example, if MailRisk highlights a surge in phishing reports, you can align your phishing simulations to focus on those specific threats, making your training more relevant and timely. Once your team is accustomed to using MailRisk, they can leverage it daily for real email threats—not just simulations.Turn the anonymous behavioral data you collect into actionable human risk metrics. These insights will show you exactly where your team needs extra support or training.
If you notice a pattern of repeated mistakes in a particular department, you can create targeted micro-courses that address those specific issues, instead of offering generic training.Use this anonymized data to streamline your compliance and certification efforts.
By having a clear, data-driven view of your organization’s cybersecurity behaviors, you can easily demonstrate your security posture during audits.
With the full Secure Practice toolkit, you’re not just piecing together isolated solutions; you’re creating a cohesive strategy that makes your HRM strategy even more manageable and effective.
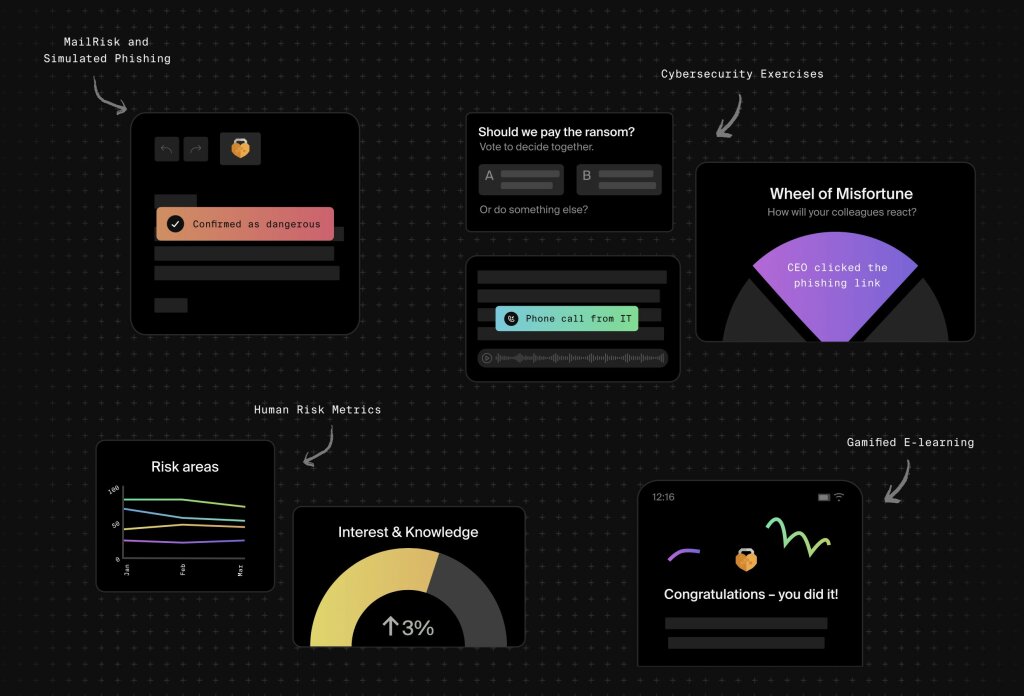
5. Learn lessons from the front lines: how companies nailed human-centric security
These companies show that when you make security personal and engaging, employees aren’t just participants—they’re your best defense. From friendly competition to real-time simulations, they’ve found ways to turn human-centric security into a winning strategy.
IBM
- Challenge
-
Struggled to get global teams excited about security training.
- Solution
-
Introduced Talent Code, a gamified training program with leaderboards and friendly competition.
- Key wins
-
Turned employees into security champions, boosting engagement and making security awareness a team sport.
- Challenge
-
Drowning in phishing emails and manual threat analysis, causing helpdesk headaches.
- Solution
-
Rolled out Secure Practice’s MailRisk to automate and streamline the process.
- Key wins
-
Supercharged their phishing defense, processing 50 times more threats without breaking a sweat, while making it easier for users to report issues.
Microsoft
- Challenge
-
Found it tough to make security training relevant across diverse roles.
- Solution
-
Customized training with real-time attack simulations tailored to different job functions.
- Key wins
-
Made security training stick, leading to more proactive and savvy employees who know how to respond when it counts.
- Challenge
-
Needed to prepare 300 managers for cybersecurity threats in a way that really mattered.
- Solution
-
Partnered with Secure Practice for a hands-on crisis simulation using real-time SMS, emails, and calls.
- Key wins
-
Brought cybersecurity to life for their managers, sparking ongoing discussions and boosting their crisis response readiness.
Looking ahead: the human threat in cybersecurity
People are an essential part of cybersecurity, and that’s a good thing. Why? Because that small fortune you invested in the latest security kit may not be protecting you as expected. Tech is a great start, but it’s the combination with human insight that turns it into a powerhouse of protection.
That said, simply ticking off training boxes won’t get you far. True human risk management demands a clever, evidence-based approach, like the one Secure Practice offers; intelligent, scientific, and proven to reduce your risk.
By tackling the real human threat in cybersecurity—cybercriminals exploiting human weaknesses—you shift the focus from blaming individuals to collectively strengthening your defenses. And when people feel valued and motivated, they start to care about security, talk about it, and—most importantly—act on it.
More efficient IT and security operations
Secure Practice helps turn your colleague’s experience into inspiration for your security program. Would you like to know more?




