Every day, your team faces countless work-related tasks and demands, and cybersecurity is often pushed to the bottom of the list. Complex training sessions filled with jargon only create more frustration, and fear-driven messages might get temporary attention, but they rarely lead to lasting change.
So how do you break through this noise? With the Think, Feel, Say, Do framework, you have the key to transforming cybersecurity education from a box-ticking exercise into a deeply impactful experience. This step-by-step approach allows you to craft training that aligns with how your team thinks, feels, and communicates about security, making it not just easier for them to understand but be something they want to engage with.
Let’s explore how this framework can help you reach your team on a deeper, more human level, frame your message to fit their everyday reality, and create a training experience that clicks.
Cybersecurity starts with empathy
IT teams are frequently understaffed and juggling a cybersecurity workload where urgency often overrides understanding. For them, the instinct is to push the harshest message, to focus on the worst-case scenarios, to hit hard with risk and consequence, because it feels like the only way to break through.
But when security communication feels like an attack—whether it’s a policy, a process, or a misstep—it can alienate the rest of your colleagues. Instead of engaging, they shut down.
Empathy shifts this dynamic. It isn't just about softening the blow or sugar-coating the facts—it’s about understanding how to speak in a way that resonates. When we start with empathy, we acknowledge the very real pressures and concerns our colleagues face, and we shape our communication to meet them where they are. It makes space for learning, curiosity, and responsibility without the fear of judgment.
As a security awareness professional, you are more than just a conduit for information; you are a translator, an advocate, and a bridge between those who manage risk and those who face it. You have the power to set the tone, to reduce tension, and to foster an empathetic work culture where those at risk feel supported, and those responsible for managing risk feel heard.
This simple shift in how and what we communicate may seem like a small adjustment, but it is the cornerstone of a more open, more thoughtful cybersecurity practice. And that’s how we turn cybersecurity from something people dread into something they embrace.
The Think, Feel, Say, Do framework in cybersecurity

The Think, Feel, Say, Do framework is a powerful tool often used in design thinking to better understand the true needs and perspectives of people.
While it may seem like an approach reserved for user experience design, it’s equally valuable in cybersecurity education, where understanding how people interact with security on a personal level is key to creating effective, lasting change.
Here’s how the Think, Feel, Say, Do framework supports your cybersecurity goals:
Emotions matter when it comes to getting buy-in for cybersecurity
At its core, this framework recognizes that people tap into their thoughts and feelings—whether conscious or subconscious—before taking action.
Just as consumers are more likely to choose products that meet their needs rather than ones that simply fulfill a want, your colleagues are more likely to embrace cybersecurity practices when they resonate with their real-world challenges, not just abstract security policies.
To communicate well, we need to know our colleagues’ perspectives
The way you communicate shapes how your colleagues perceive cybersecurity—not just as a process or a set of rules, but as something personal, something they either connect with or resist. But, if you don’t know what they already believe about security or how they feel about their role in it, you might need to shift our approach from telling and showing to asking and observing.
Incorporating the Think, Feel, Say, Do framework for cybersecurity into your work prompts you to pay attention not just to what people are saying, but also to how they're reacting. If someone claims to follow security protocols but shows signs of frustration, the framework helps you dig deeper into those feelings and address them. It helps you ask the right questions and really listen to what they’re saying (and not saying).
This way, you can uncover their true feelings and challenges, giving you a better understanding of their experience and how you can incorporate it into your training.
Listening to people helps us shape better security programs
Together, the four quadrants of the framework create an empathy map, giving us a roadmap for understanding human behavior beyond surface-level actions.
It’s relatively easy to observe what one of your co-workers says or does during a security training or incident. For instance, they may say, "I always follow password policies," or they might complete a mandatory training session.
But here’s where the deeper insights come into play: what someone thinks or feels about these actions can tell a much richer story. Maybe they completed the training, but internally, they felt frustrated or overwhelmed. Or perhaps they thought, "This doesn't apply to my role," while outwardly complying with the instructions.
By carefully analyzing these behaviors, you can tailor your communication and training to address their real needs—not just the compliance checkboxes—and shape security programs that feel relevant and supportive, rather than burdensome.
To get a clearer picture of what your colleagues really think and feel, you need to observe how they behave and respond in different scenarios. For example:
Do they appear distracted or disengaged during training?
Do they raise concerns privately?
Do their actions show they’re cutting corners because they feel security is too complex or time-consuming?
How empathy maps make cybersecurity personal
Empathy maps provide a way to sum up what we’ve learned from conversations, behaviors, and feedback, allowing us to design more relevant stories, narratives, and journeys.
As you use empathy maps, you begin to visualize and understand how colleagues think, feel, and act, by highlighting not only their actions but also their underlying motivations, insights, and barriers.
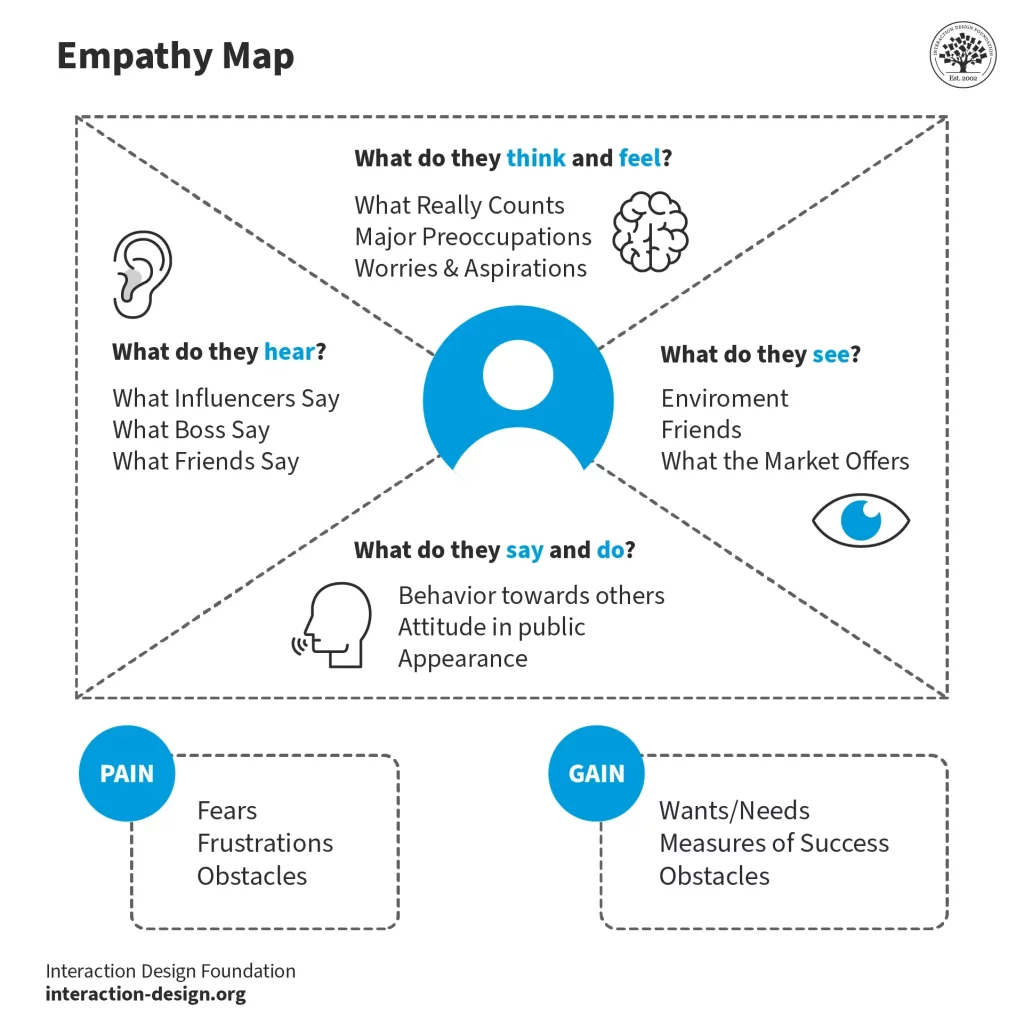
An empathy map helps illuminate what matters most to your colleagues—and why. For example, if they’re anxious about failing a phishing test or see password policies as tedious, the map brings these concerns to the surface. As you empathize, you can work backwards and craft a message that meets them where they are, using a narrative that resonates emotionally and practically.
Empathy maps highlight the personal and emotional connections people have with cybersecurity.
Many people in this space—whether it’s their job or just a personal interest—are drawn to the idea of being protectors, almost like modern-day vigilantes or superheroes, defending the vulnerable and bringing justice. This narrative could be incredibly powerful in shaping how you engage them: cybersecurity isn’t just about following rules; it’s about protecting your team, being vigilant, and doing the right thing.
For those who might feel overwhelmed, an empathy map allows you to reframe cybersecurity education as a practice that mirrors the values every company wants to foster—helpfulness, constant learning, doing the right thing, and having each other’s backs.
Using empathy to connect with colleagues
Meet Alex, a marketing coordinator that thinks:
“What if I fail the phishing test? I’m already overwhelmed.”
Think: Alex worries that her busy schedule leaves little time for cybersecurity training
Feel: She experiences anxiety about the pressures of compliance
Say: Alex expresses frustration, “I always follow the rules, but this feels too complicated”
Do: She may avoid security tasks, fearing they’ll add to her stress
Crafting empathetic responses
As cybersecurity professionals, we can respond with empathy.
“We understand your workload is heavy. Here’s a simple guide to updating passwords quickly, so you can focus on what matters.”
By framing our messages in a way that acknowledges her challenges, we help Alex see cybersecurity not as a chore, but as a part of her teamwork in protecting the organization.
How to use the Think, Feel, Say, Do framework to make training meaningful
Many people come into cybersecurity training with a stereotype: endless, jargon-filled modules that feel overwhelming. But you can change that perception with experiences that truly matter.
With the Think, Feel, Say, Do framework, you can focus on content empathy instead of sheer volume. This approach simplifies your colleagues’ learning experience, breaking it down into smaller, relatable moments that fit into their busy lives. It’s why we at Secure Practice offer customized training and tools that are tuned to each person’s role, responsibilities, knowledge, and interests—smart, targeted cybersecurity training at its best.
Next up, we’ll guide you through a step-by-step tutorial on creating an empathy map and using the Think, Feel, Say, Do framework to design training that resonates with your team’s needs.
Step 1: assemble your empathy map
Creating an empathy map is a collaborative effort that sets the stage for understanding your colleagues' experiences with cybersecurity training. It tunes you into their perspectives, feelings, and behaviors, which helps you choose immersive experiences, intuitive tools, and engaging learning materials that work best for their specific needs.
Set up your map
Gather your team: bring together a diverse group of team members—think about including someone from different departments, as well as leadership. A meeting room buzzing with discussions as your HR colleague shares insights about employee concerns, while your IT counterpart highlights technical challenges they’ve observed sets the groundwork for rich discussions.
Draw the map: set up four quadrants labeled “said,” “did,” “thought,” and “felt” to create a basic empathy map template. As you draw the quadrants, visualize them on a whiteboard in the office, where everyone can see and add sticky notes or comments, sparking lively conversations. This visual aid keeps everyone engaged and encourages contributions from all team members as you fill it out.
Fill our the quadrants
Said
Let’s start by collecting direct quotes or feedback from your colleagues about their experiences with cybersecurity training. You might hear things like:
“It’s too complicated.”
“I don’t see how this affects me.”
“The last training felt like a snooze-fest.”
“I didn’t get how this applies to my day-to-day tasks.”
These sentiments reveal a disconnect between cybersecurity practices and their actual roles.
Did
Next, observe your colleagues’ behaviors during training sessions. For instance:
Are people frequently checking their phones?
Are they actively participating and asking questions?
Do you notice colleagues joking about phishing emails, suggesting they don’t fully grasp the risks involved?
These observations can give you a deeper understanding into how engaged they really are.
Thought
It’s crucial to consider the unspoken thoughts colleagues might have. Many may think:
“Cybersecurity isn’t my job.”
“I won’t be the one hacked.”
“I don’t have time for this.”
“I’m not tech-savvy enough.”
Recognizing these thoughts helps you understand why they may not feel personally connected to cybersecurity responsibilities.
Felt
Lastly, let’s identify the emotions your colleagues experience. They might feel:
Anxiety about making mistakes in their cybersecurity practices.
Frustration over unclear policies or expectations.
Acknowledging these feelings is key to developing a supportive training environment.
Step 2: uncover your real training needs and gaps
Once you’ve filled out the empathy map, the next step is to synthesize the information to pinpoint your colleagues’ real cybersecurity needs. This process transforms raw data into actionable insights.
Translate insights into needs: look for common themes that emerge from the quadrants. This will help you frame specific needs for your training programs. For example, if multiple colleagues express feeling overwhelmed by training, you could conclude that there’s a need for more digestible, bite-sized training materials that simplify complex topics.
Spot contradictions: identify any contradictions between what colleagues say and how they behave. This can highlight deeper needs. If people say they want more training but seem disengaged during sessions, it may indicate a need for more relevant and engaging training experiences that better align with their daily challenges. It’s about aligning what they say with what they do.
Step 3: turn your insights into action
With a shared understanding of your colleagues' needs, you can now develop practical solutions that respect their attention spans and resonate with their real-world challenges.
Tailored training programs: use what you’ve gathered to design training sessions that address specific concerns. For instance, if feedback indicates that training feels overwhelming, consider creating shorter, focused sessions on relevant topics, like simulated phishing that mirror real-life scams people encounter regularly.
Utilize storytelling: craft narratives that illustrate real-world scenarios where good cybersecurity practices have made a difference. Share a story about how one of your colleagues caught a ransomware attempt that could have compromised company data. This not only makes training relatable but also underscores its importance.
Create a feedback loop: make sure to encourage ongoing feedback about your training sessions. Simple tools like surveys or suggestion boxes can help you adjust your approach based on real-time insights directly from the people it’s helping, keeping the training relevant.
Step 4: use the Think, Feel, Say, Do framework to improve training and cyber resilience
Now, let’s apply the Think, Feel, Say, Do framework to enhance engagement and make cybersecurity training resonate with your colleagues.
Think: change the way colleagues look at cybersecurity
Most people don’t think cyber threats apply to them. It’s something that happens to other companies, in some distant corner of the internet. But cyber risks are personal, and making them relatable is the first step in changing employee behavior.
Start with a clear understanding of what your colleagues are thinking. Use insights from the “thought” quadrant to frame your training, emphasizing how their roles connect to cybersecurity and why it matters.
To help them think differently about the impact of a phishing email or a weak password, show how these small decisions can lead to real-world consequences for their team and customers. Your colleagues should understand not just what a cyber threat is, but how it endangers their immediate environment.
Break down the risks into stories and examples they can relate to in their own roles:
- Intrusive thought
-
“Cybersecurity isn’t my job.”
- Real-world consequence
-
For someone in HR, a breach of payroll or personal information could damage trust and also lead to severe legal and financial repercussions.
Every HR email or document containing sensitive information is a potential risk factor.
By adopting safe practices, like secure file sharing, you’re actively protecting both employees and the organization.
- Intrusive thought
-
“I won’t be the one hacked.”
- Real-world consequence
-
In Sales, you’re handling sensitive but valuable data like financial and customer records every day, making you a very attractive target for cybercriminals.
A single phishing email could compromise an entire client’s portfolio, damaging both your reputation and your relationship with key accounts.
By staying vigilant, you’re not just protecting the company—you’re ensuring that client trust remains intact.
- Intrusive thought
-
“I don’t have time for this.”
- Real-world consequence
-
As a project manager, you juggle tight deadlines and multiple stakeholders. It’s easy to feel like there’s no room for cybersecurity concerns.
But imagine the setback if your team’s work was compromised because of a data breach. Taking a few seconds to verify a suspicious email or making sure sensitive project files are shared securely can save hours of recovery time later on.
Cybersecurity isn’t a time sink—it’s a way to safeguard the momentum of your work.
- Intrusive thought
-
“I’m not tech-savvy enough.”
- Real-world consequence
-
For a finance team member, handling transactions and confidential financial information comes with inherent risks. Cybercriminals are increasingly targeting financial operations through schemes like wire fraud or invoice tampering.
You don’t need to be a tech expert to safeguard these processes—something as simple as double-checking unusual requests or using multi-factor authentication on financial accounts can prevent costly errors.
Protecting the company’s finances starts with basic security habits.
By breaking down abstract threats into relatable scenarios, we help people see that cybersecurity is part of their everyday responsibilities, rather than an IT problem to be outsourced.
Bite-sized tip
How you talk about cybersecurity risks matters. Rather than sternly warning colleagues, "Don’t click suspicious links," add an empathetic touch that makes cyber risks real and relatable: "This link could compromise your entire department’s data—here’s how to spot a risky one."
Feel: address emotional barriers in cybersecurity education
How do your colleagues feel about cybersecurity? For many, the answer is overwhelmed, confused, or even scared. Fear-based approaches—“don’t do this, or you’ll compromise everything!”—only fuel anxiety and create distance.
But cybersecurity doesn’t have to be intimidating. To lead with empathy, we must reframe it as something that protects colleagues, not as something designed to catch or punish mistakes. This means using softer, more encouraging language and acknowledging the anxieties many colleagues have about security practices.
Anxiety about making mistakes in cybersecurity
- Instead of
-
“If you click on a phishing email, you’re putting the entire company at risk.”
- Try this
-
“We understand that phishing emails are tricky. Here’s a simple way to spot them so you can help protect your team and our company from potential threats.”
Frustration over unclear policies or expectations
- Instead of
-
“You need to follow these security policies exactly as outlined, no exceptions.”
- Try this
-
“We know some security policies can seem complicated, but they’re in place to protect your work. Let’s break them down together so you know what’s expected.”
Feeling overwhelmed by technical details
- Instead of
-
“Just follow the protocols—it’s all laid out in the training materials.”
- Try this
-
“We understand security can feel complex, but we’re here to help simplify it. Here’s how you can protect yourself and the company with just a few simple steps.”
Concern about cybersecurity feeling like extra work
- Instead of
-
“You have to prioritize security, no matter how busy you are.”
- Try this
-
“We know you’re busy, but these small steps can protect your work without slowing you down. It’s a quick way to safeguard everything you’ve worked hard on.”
Fear of reporting mistakes and facing punishment
- Instead of
-
“If you make a mistake, it could lead to a security incident. You need to be more careful.”
- Try this
-
“Mistakes happen. Reporting them quickly helps prevent bigger issues. By speaking up, you’re helping protect the team and keeping the company safe.”
Confusion about role-specific security expectations
- Instead of
-
“You should know by now what your cybersecurity responsibilities are.”
- Try this
-
“Cybersecurity expectations can feel unclear sometimes. Let’s go over what’s most important for your role so you feel confident moving forward.”
Bite-sized tip
At Secure Practice, we believe in making cybersecurity a positive experience, and our tools help address emotional barriers while keeping your colleagues engaged. Here’s how:
Ease anxiety with cybersecurity exercises that gently guide your team to reinforce good habits without the pressure. It’s all about practice in a safe space!
Clear up confusion using gamified e-learning modules. These fun, interactive lessons make understanding policies easy and engaging, so no one feels lost or bored.
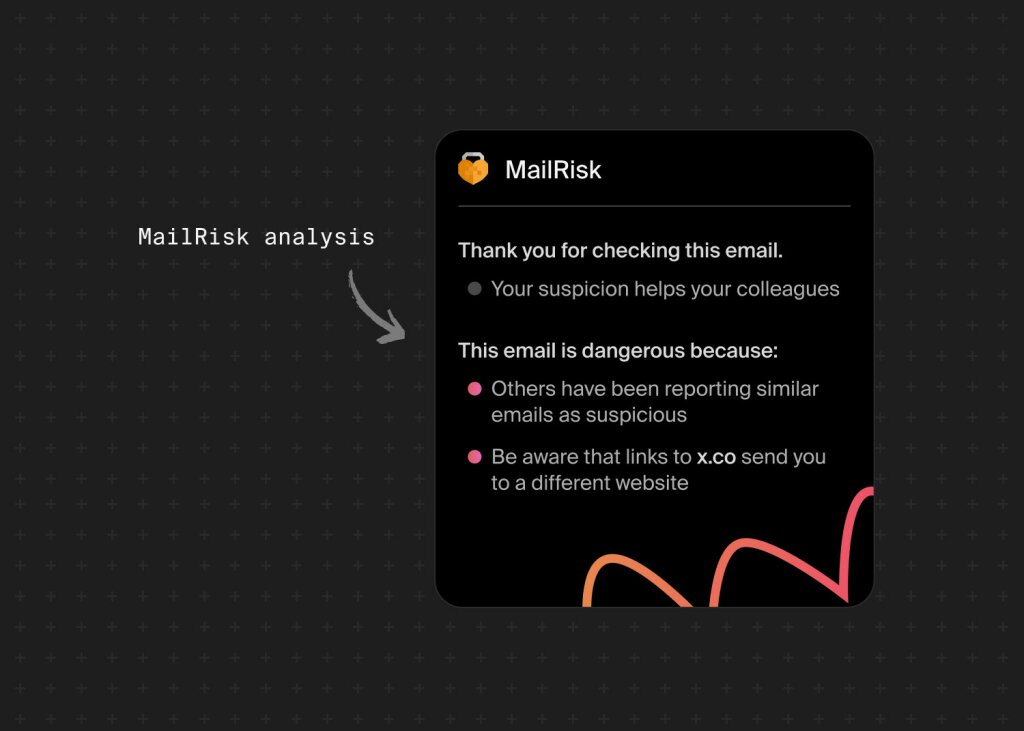
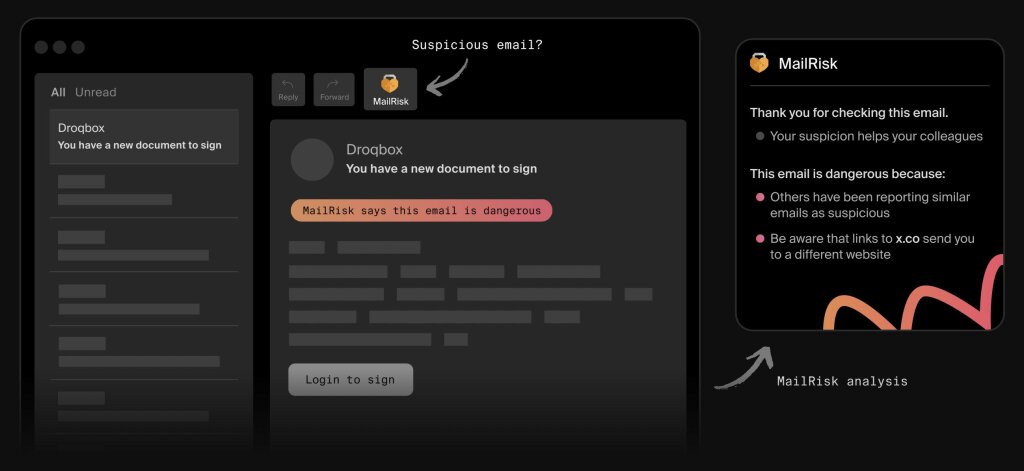
Make security part of the daily grind with MailRisk, which gives friendly feedback and insights to keep everyone aware without interrupting their workflow.
Create a culture of safety with simulated phishing exercises that let your team practice spotting threats in a non-threatening way.
It’s all about learning together. Discover how Secure Practice can make cybersecurity feel like a team effort.
Say: build two-way communication with your colleagues
Traditional cybersecurity education is often a one-way street: IT teams tell employees what to do, and employees either comply or don’t. But real cybersecurity culture grows when there’s an open dialogue, where employees’ concerns are heard and their feedback is valued.
The "Say" element of the framework is about listening to how the people around you talk about cybersecurity and integrating their experiences into daily habits. This means creating ongoing, two-way communication where employees feel safe reporting issues and are empowered to adopt secure behaviors that fit naturally into their workday.
Here’s how to reframe what your colleagues may have said during your research, making them partners in risk management rather than passive recipients of blame:
“It’s too complicated.” If you hear this, it’s a great opportunity to simplify things. Instead of bombarding them with tech jargon, try breaking down those complex ideas into everyday language. You could even follow up with a quick survey to see if the changes helped. This shows your team that their voices matter and encourages them to keep sharing their thoughts.
“I don’t see how this affects me.” When someone says this, take a moment to chat with them about their specific role. Maybe set up a casual roundtable discussion where team members can talk about how security practices play into their daily tasks. It’s a great way to highlight the importance of cybersecurity while creating a collaborative vibe where everyone feels included.
“The last training felt like a snooze-fest.” Ouch, right? But this feedback can be super valuable! Use it as a chance to shake things up by adding some interactive elements like quizzes or group activities to keep things lively. And invite your colleagues to share their ideas for making training more engaging—it will show them that their input can really shape the experience.
“I didn’t get how this applies to my day-to-day tasks.” This is a cue to get creative. After hearing this, why not create training sessions that tie directly to what folks do every day? Involve your colleagues in the planning by asking for their input on real scenarios they encounter. This way, you make the training relevant, and it strengthens their connection to their own responsibilities.
Bite-sized tip
Create a “Cybersecurity Suggestion Box” where colleagues can anonymously share their thoughts on training sessions. This encourages honest feedback and helps you gather valuable insights to make improvements that resonate with their needs.
Do: integrate cybersecurity into everyday work life
Cybersecurity education doesn’t happen just in annual workshops or through a list of rules that get buried in email. The most effective education happens in everyday moments.
Instead of relying on formal training sessions alone, think of ways to integrate cybersecurity into the work environment:
- Observation
-
Colleagues are frequently checking their phones during training sessions.
- Recommendation
-
Use engaging visual reminders
- Example
-
Place colorful, eye-catching posters in common areas that highlight key cybersecurity practices, such as “Think Before You Click” or “Password Tips.” These reminders can grab attention and reinforce secure behaviors throughout the day.
- Observation
-
Some colleagues may not know where to report suspicious emails or incidents.
- Recommendation
-
Establish clear reporting channels
- Example
-
Create a simple infographic that outlines how to report suspicious emails or security concerns, and post it in high-traffic areas (like bathrooms). Then, use our MailRisk feature to provide a quick way for employees to report issues directly from their inbox, ensuring everyone knows the process and feels comfortable taking action.
- Observation
-
Colleagues aren’t actively participating and asking questions during training.
- Recommendation
-
Incorporate quick cybersecurity updates in meetings
- Example
-
Dedicate a few minutes in team meetings to discuss a recent cybersecurity threat or share a tip. For example, “This week, we learned about a new phishing tactic; here’s how to spot it!” This keeps cybersecurity relevant and top of mind. Complement this with Secure Practice’s simulated phishing reports, discussing real-world examples to keep cybersecurity relevant and top of mind.
- Observation
-
Colleagues seem to forget important cybersecurity protocols after training sessions.
- Recommendation
-
Break down complex presentations into bite-sized pieces
- Example
-
Micro-training sessions, visual cues, and friendly resources in various formats make cybersecurity a daily habit, just like getting coffee. Pair this with gamified e-learning modules to create a friendly competition where teams earn points for completing challenges, like identifying phishing emails or answering quiz questions. Offer small rewards for engagement, reinforcing learning in a fun way.
- Observation
-
Colleagues often rely on IT for every cybersecurity concern.
- Recommendation
-
Empower employees with self-service resources
- Example
-
Develop a cybersecurity knowledge hub on the company intranet featuring Secure Practice’s training modules and resources. Encourage employees to explore these self-service options before reaching out to IT, fostering independence and confidence in handling common issues.
Bite-sized tip
Human risk metrics help you understand the specific challenges your colleagues have, without having to sacrifice their privacy. This helps you:
Recognize your team’s security real needs and upgrade your cybersecurity program to reflect them
Craft bespoke, positive learning journeys that respect colleagues’ pace and privacy
Customize training for specific roles so it feels relevant and relatable, helping your colleagues connect their everyday tasks to the bigger cybersecurity picture
Spot the eager learners and the savvy skeptics, and tailor their learning journey to fit their needs
Create tailored follow-ups like micro-courses or exercises, ensuring upskilling aligns with evolving needs
Leading cybersecurity with empathy is leading with trust
Empathy isn’t just about understanding; it’s about creating a culture where everyone feels trusted to make smart security decisions. When your colleagues see that their efforts matter and that they’re part of something bigger, they’ll naturally be more inclined to take those important security steps.
The Think, Feel, Say, Do framework helps us bring structure to complex emotions, reactions, and thoughts that often go unnoticed in the rush of daily tasks. It allows us to connect the dots between what colleagues think, feel, and do, creating a more supportive, responsive environment for cybersecurity. When we acknowledge and understand these underlying emotions, we can shape security practices that aren’t just effective, but that people want to follow.
At the heart of this is empathy—not just for the people we’re protecting, but for ourselves, too. The fact that you’re reading this and looking for ways to improve shows your commitment. It’s okay to feel overwhelmed at times, but remember that your efforts to bring empathy into cybersecurity make a real difference.
To get there, your colleagues need:
Tools that blend into their daily practice
Knowledge they can use throughout their lives
Learning experiences that stay with them
Feedback on how they’re making a difference
That’s what we focus on at Secure Practice—providing tools and training that fit naturally into your team’s daily routine, respecting their time, energy, and attention.
In the end, we all share the instinct to stay safe and protect others. With the right support, your colleagues can tap into that instinct and become empowered, confident participants in your organization's security. Let’s make sure they have the tools, context, and guidance they need to do that—and recognize the effort you're putting in to make it happen.
Get your colleagues to care about security
Explore Secure Practice’s human risk management solutions and help people discover they can use their existing skills and know-how to make good security decisions.