Have you ever received an email and wondered if it could be dangerous? It is definitely a good idea to report the suspicious email to IT, but the usefulness of your reporting increases if you are able to analyze the email headers.

Headers are metadata which will reveal e.g. where the email originated from, which servers it has been forwarded by on its way to your inbox, and whether or not the sender's web domain has passed a basic fraud check.
IT will usually benefit from receiving these data, if one should find out whether the email is safe or potentially dangerous.
The most common approach is to forward the email with the usual Forward button, or maybe just send a screenshot. The downside to this is that a lot of «invisible» content from the original email will disappear, its so-called message headers.
Here follows to methods to forward the suspicious email to IT in the rightway:
Copy message headers
Behind a properly hidden menu in Outlook, you can find a way to reveal the original message headers for an email. Although it is not user friendly at all, this recipe will make sure you get the job done.
First step is to double click the suspicious email (1) in your message list, so that it gets opened in a separate window:
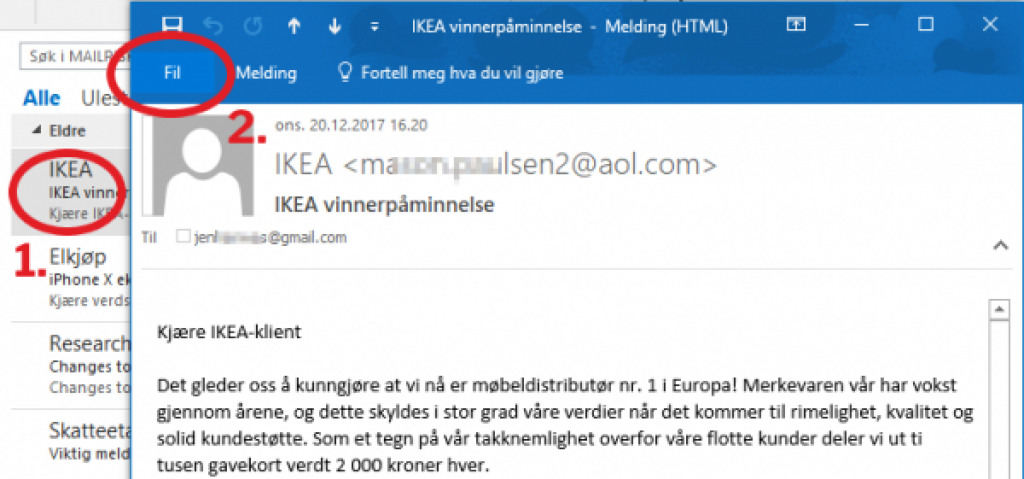
Then, click "File" (2.) in the message window to reveal a number of new options. Scroll down to the bottom of this page, and click the "Properties" button (3.):
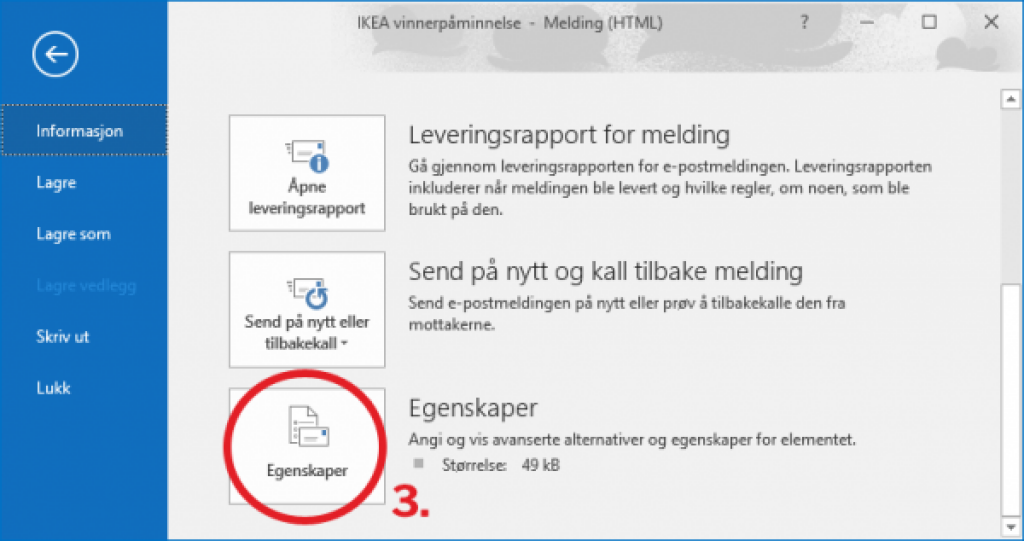
Finally, a new window will open with a number of settings. What we are looking for is however located in the small text box towards the bottom (4.):

Click your cursor inside this text box, to enable the text marker. Now you can click CTRL + A on your keyboard to highlight the entire text, and then CTRL + C to copy to your clipboard.
Finally, you may now go back to the email, click "Forward", and paste the message headers at the bottom of the email with CTRL + V on your keyboard.
This method however only works in Outlook on a Windows PC, and is not available for Mac or mobile users.
MailRisk makes this simple
Luckily, there are better ways to get help with suspicious emails.
MailRisk is an add-in for Outlook which solves any analysis and data collection needs with a simple click.
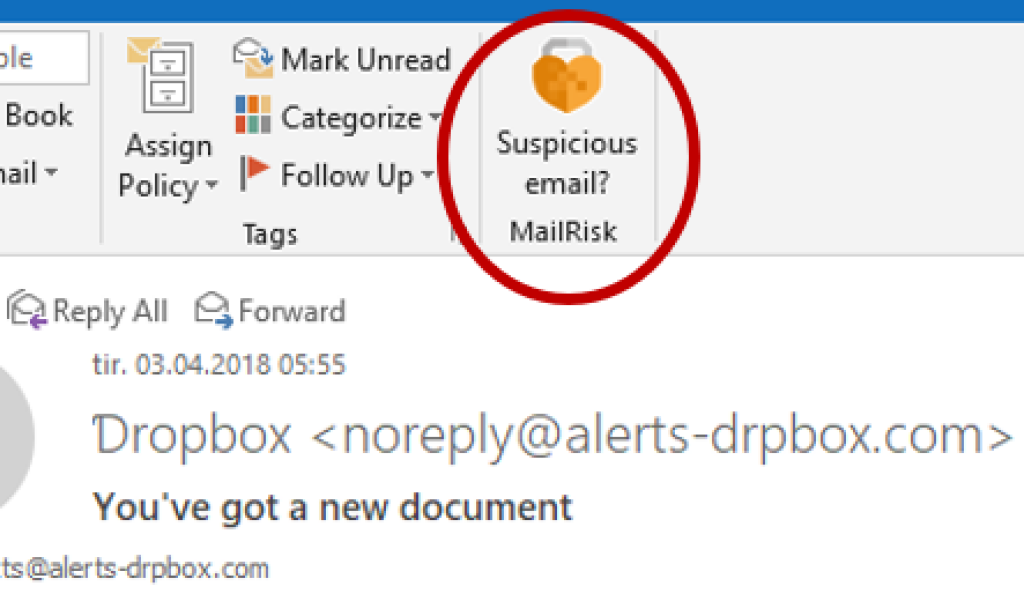
When analyzing the email, you may also find out whether the email is safe or not. This way, you can always obtain a second opinion, even if this includes the request of a manual analysis performed by a security expert.
See the movie about how MailRisk helps you with stopping scammers and hackers:
MailRisk also makes it easy for IT to stay on top of every email which is reported by their colleagues. Our robot will ensure that report which have certain things in common will be grouped and categorized, and intelligence on currently unmanaged threats becomes available for targeted mitigating actions.
In addition, MailRisk works just as well on both PC, Mac, webmail, tablets and mobile.
Could MailRisk be useful to you and your colleagues? Learn more →

