The email has invites@microsoft.com as sender, and every technical investigation (both SPF, DKIM and DMARC) shows that the email itself has indeed been sent from Microsoft.
Every link in the email goes to Microsoft as well. Still, something is not entirely right, because the OneDrive logo is (currently) not entirely up to date:

When you click the main button "Get started", you land on a legitimate landing page for Office 365 users. If you are already logged in here, you will first be asked to approve that "OneDrive for Business" is granted access to log you in, and read your name, email address and profile picture.
And after this, you may end up at an arbitrary URL, within the attacker's control.
Since every invite link is personal, it is however not possible to reveal what is in fact behind another user's invitation. Therefore, we have tried to create a similar campaign to figure out which possibilities an attacker may have with this technique.
Azure Active Directory B2B Collaboration
The service which can be abused is in many ways a very useful service from Microsoft, which allows companies invite external users from other companies into their internal spaces, but where the external user can login with thei ordinary Office 365 user account.
An attacker may however create a free trial for Azure AD Premium, and get access to the very same functionality. If you here name your Azure AD organization as e.g. a well known brand name (like OneDrive for Business in the example above), you may also add a logo which will be used in the header of every email which is being sent out to new users.
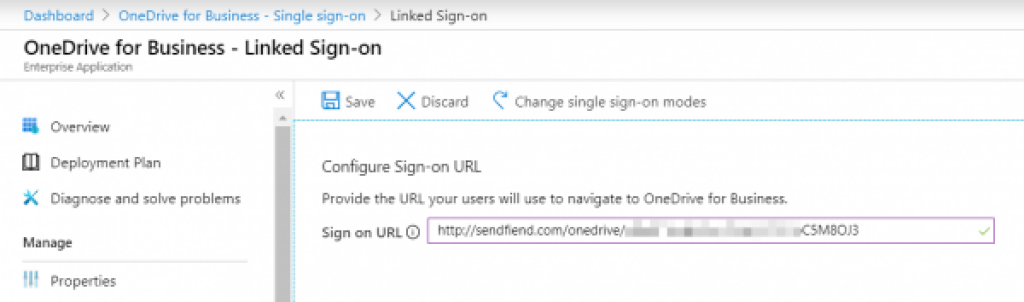
From here, you may create a so-called "Enterprise App" in this organization, and then say that this application shall offer single sign-on through a user defined URL, which is potentially the attacker's own website:
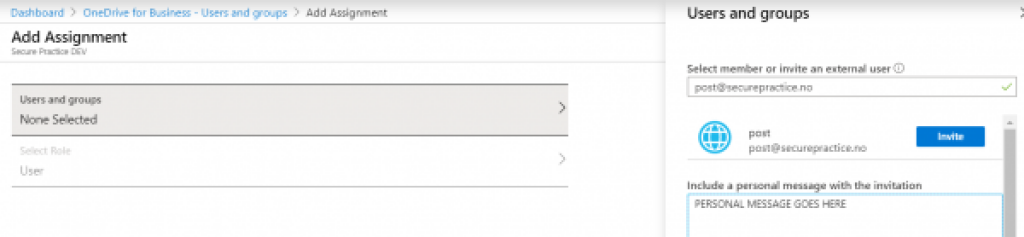
This application can further be assigned to new users, and this is where the attacker can insert phishing recipients. There is by design full access to provide external email addresses here:
When clicking the "Invite" button, the malicious invite will now be sent - from Microsoft. When the recipients choose to accept the "invite", they will end up at the application's landing page

From here will any click on the application in question take the user to the attacker's own login page, or any other resource which is provided for single sign-on support:
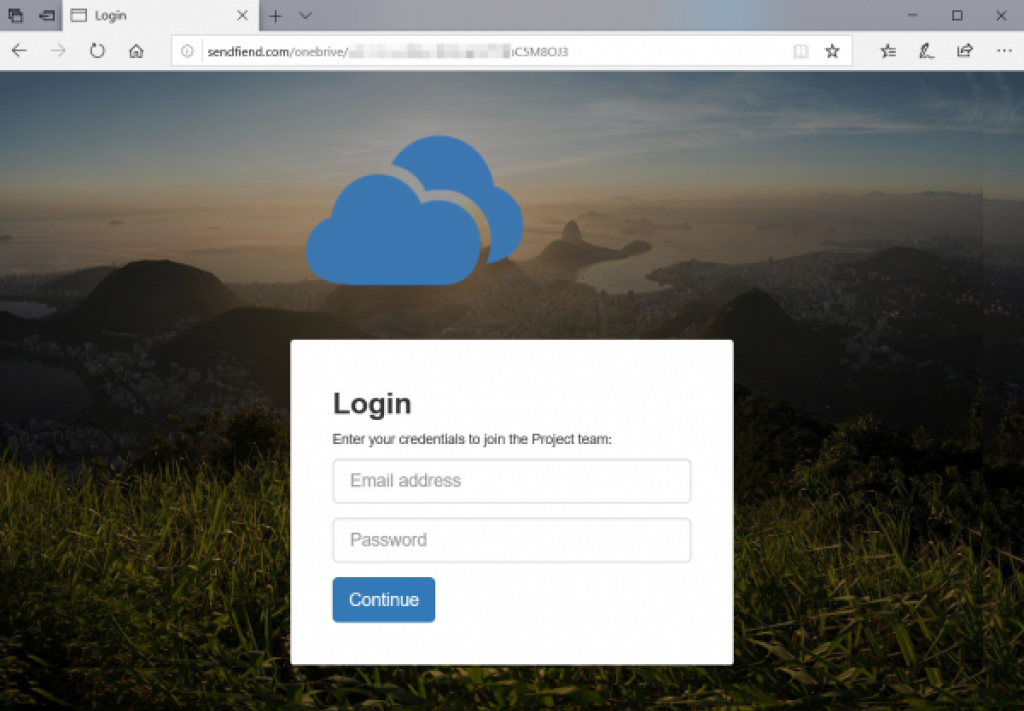
The screenshot above is for the record not the actual phishing campaign we detected through our customers' use of MailRisk. It is instead a landing page which we offer through our own phishing simulator.
In order to protect your organization's users against this particular attack scenario, consider blocking the access users have to approve data sharing from their own company user towards external (multi tenant) applications:
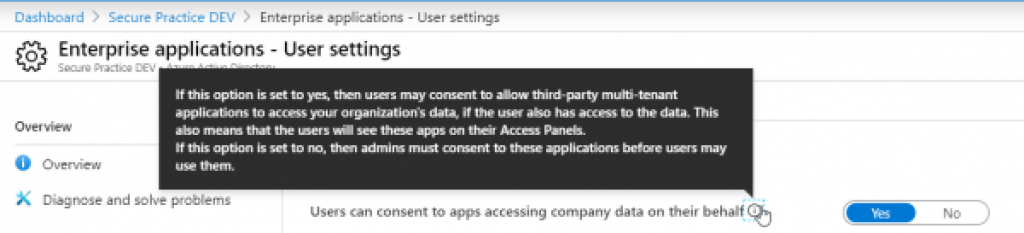
Please note that this setting may also get in the way of legitimate usage scenarios for such authentication. At the same time, this configuration setting makes it unlikely that abuse of the service can be called a “vulnerability” from Microsoft's side.



