Does your website allow the forwarding of end-users to URLs provided as a user-provided URL parameter? If so, it may potentially be abused in phishing campaigns, along with your web domain reputation.
When spam filters check incoming emails, one of the common things to assess is the so-called reputation of any web domains which are linked to in the email.
As a consequance, cybercriminals are naturally looking to abuse the reputation of your legitimate web domain for their own malicious purposes. Sometimes this involves hacking your website to install their own content on your public URL, but this is not always the easiest way.
Recently, we've seen a surge in phishing attacks which take advantage of a particular kind of website functionality, namely redirects.
Redirect implementations
Redirects are used with several various implmentation for each their purposes:
URL shortening (e.g. https://aka.ms/securitybaselines) for brevity and rememberability;
Dynamically changing content behind a given link, to ensure up-to-date content without broken references when included in e.g. product advertisement, packaging, or software code (e.g. http://go.microsoft.com/fwlink/p/?LinkId=255142);
Sending users to a specific resource after successfully being authenticated (e.g. https://accounts.securepractice.co/login?return=https%3A%2F%2Fmanage.securepractice.co%2Fauth).
Tracking response on shared links, especially on social media posts, even when your company's post links to an external website, similar to how Google forwards users to search results (e.g. https://www.google.com/url?rct=j&url=https%3A%2F%2Fsecurepractice.co%2F).
Abusing redirects for phishing
Consider especially the two last examples above, which can be prone to exploitation. Since they both take a full URL as their input from the user, an attacker could equally insert their own malicious URL and embed the redirect link in a phishing email.
The following is a real example where a trusted telecom provider has been abused to forward recipients to the attacker's website. Notice how the "rd" URL parameter contains this target:
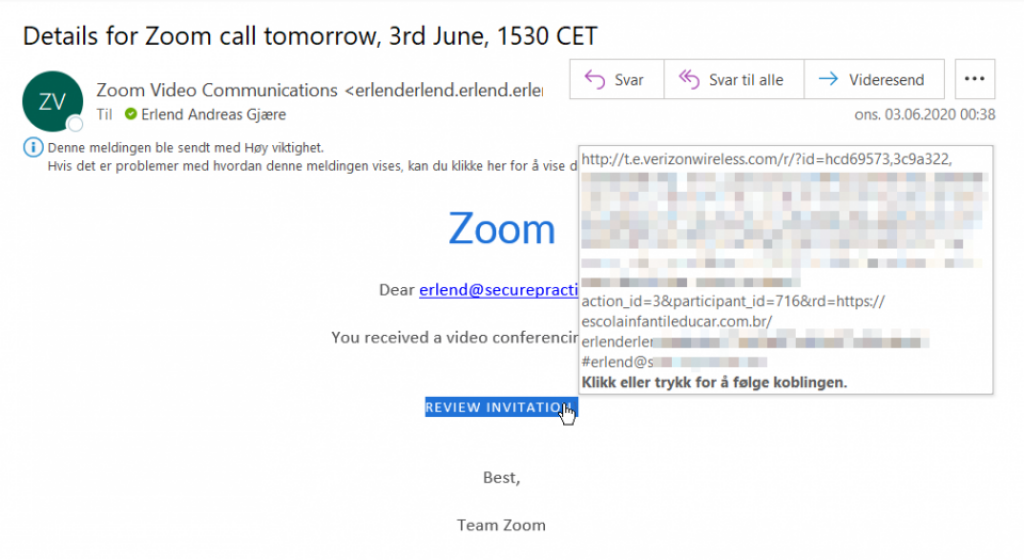
Any phishing campaign will benefit from abusing such open redirect services, making their emails much easier to deliver. A spam filter will evaluate the linked URL, and simply find a legitimate website, since it cannot understand the nature of redirect parameters.
Protecting against abuse
Luckily, there are several ways to mitigate such attacks which abuse your infrastructure. Consider the four examples, and you will find that the first two from Microsoft implement an identifier lookup where arbitrary input cannot be provided.
The third example is commonly used in login services as shown. In these cases, it should be required that particular target domains to be flagged as safe, while any other redirect domains are denied.
The final example shows how Google try to mitigate abuse, by showing an intermediate landing page which tells the user about the redirect. Landing pages like these could very well inform the user about the risk of proceeding, but are better to avoid entirely, if possible.
It may however be that emails are already making their way beyond your spam filter, reaching the inboxes of your end users. Our MailRisk add-in for Outlook will already warn the recipient if many such redirects are present in an email, since the likelihood of abuse is so prominent.
In any case, make sure you are aware of the presence of any redirect functionality in your company's website: Try inserting another webdomain in your redirect, and check out what happens. If an external redirect goes through, you may have a domain name reputation risk to mitigate as well.
For further reading, check out the OWASP cheat sheet on unvalidated redirects and forwards. You could also try the Oralyzer tool which uses automated fuzzing to detect open redirect vulnerabilities in a given URL pattern.



