QR codes thrived as a contactless way to order food and pay during the pandemic, and have also been used in advertising and event tickets for quite some time.
And now, QR codes are becoming really popular among hackers and scammers, too.
Remember holding up your phone towards the screen, scanning a QR code, to enable two-factor authentication on your user account?

Setting up two-factor authentication on a new device or account is probably not something you do every day.
But you probably knew it was very important that time when you did it.
And scammers really know how to take advantage of both of these facts.
Fake Authenticator QR scans
What if you received an e-mail from your organization's IT-staff, telling you about a security alert relating to your account? «Scan the QR code to receive mandatory security updates for your authentication app.»
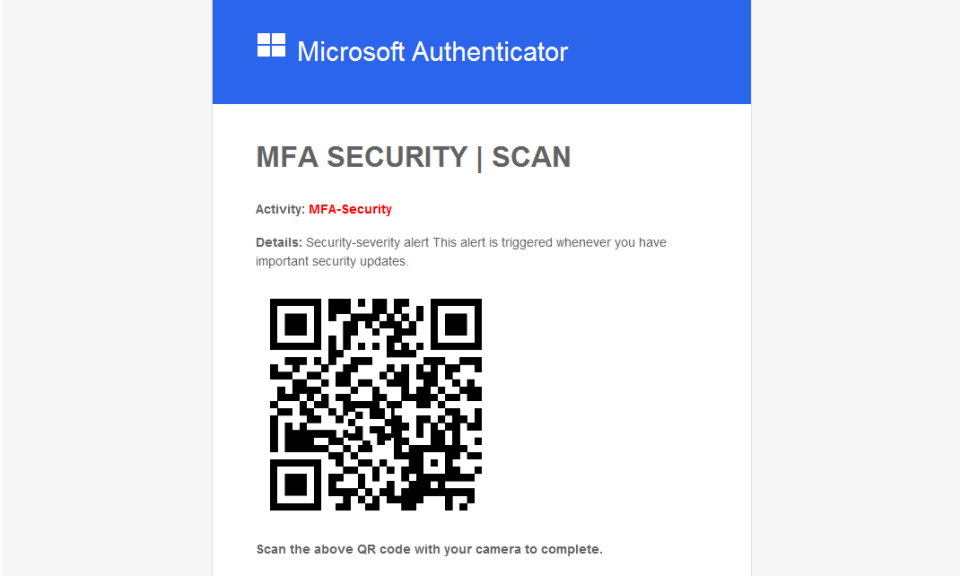
Scanning a QR code may seem safer than clicking a regular link, as there is no obvious suspicious link visible.
However, a QR code is essentially a link. The pixelated QR pattern is just a representation of text in a visual format, which machines can easily read.
A QR code can therefore direct you to any website chosen by the scammer, such as a fake Office 365 login page, as in the example above.
In the next step, it would seem logical to log in with your username and password to supposedly update security information on your account.
Except, there is a hacker on the receiving end who can now steal your login information.
Security detection may be scarce
In the same way that people and organizations are getting better at spotting and recognizing classical phishing attempts, malicious actors are also improving and changing their methods of attack.
Fake two-factor authentication updates are not the only trend we are currently seeing. QR codes are now frequently replacing the links typically found in traditional phishing emails.
For example, a QR code might be used to promote something like "Employee benefit eligibility enrollment," which many people may find attractive to learn more about:
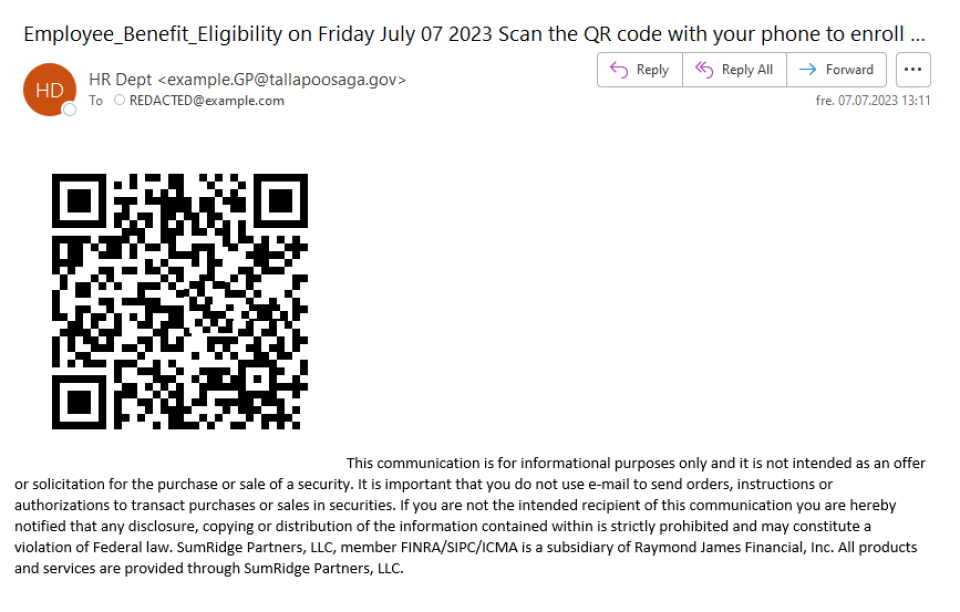
(Please note that we have distorted all QR code examples in screenshots, so that readers of this article will not actually end up on dangerous websites.)
What hackers cleverly do here is exploit the fact that when you proceed with links like these via your mobile phone, you are less likely to be protected by both detection on your device and your organization's network monitoring.
Spam filters, which can usually identify dangerous emails before they are delivered to your inbox, typically do not scan links presented as QR codes.
Additionally, anti-virus and VPN are mainly security features used with laptops and are less commonly seen on (partially) private or personal devices in the mobile network.
Since this kind of attack bypasses many automatic security features, it leaves you in a situation where you need to think critically for yourself.
In reality, anyone can create QR-codes, and they can become even more dangerous with a bit of social manipulation.

Luckily, since you are reading this, you may already be familiar with our MailRisk button in Outlook. It can always tell you whether an email in your inbox can be trusted, regardless of whether it contains QR codes or old-fashioned links.
You may come across the term «Quishing»...
Due to the increasing popularity of using QR codes for phishing, security professionals are eager to find a new word to describe the new phenomenon.
You may therefore encounter the term "quishing", which is short for "QR phishing".
However, the word in itself does not carry any inherent meaning, and you should not be surprised if people who have not read this article do not know what quishing is.
Making security difficult by using difficult words will only make it more difficult for people to be confident, when facing security decisions like whether to proceed with a «mandatory security update to your authentication app».
For our part, we will call it QR code phishing (or phishing with QR codes), to make it more obvious what we are talking about.
Just like we prefer calling phishing via voice (not «vishing»), and phishing via SMS (not «smishing») by what they actually are.
We can only imagine what's next.
(Open the camera app on your phone, and scan the QR code below to find out 😇)
